Vendor Risk Management
Onboard vendors in hours, not days. Manage workflows, not spreadsheets. Accelerate productivity, not risk.
Manage the entire vendor lifecycle in one place.
Vendor Risk Management helps risk and security teams remove the complexity of managing a growing vendor portfolio. From building your third party inventory through automated invitations, to consolidating document collection in one dashboard, to continuously assessing vendor security hygiene, it is purpose-built for those charged with managing an organization’s greatest risk: it’s vendors.
Watch the video for a quick walk-through.
40K
Vendor profiles
3x ROI
Within first six months*
90%
Vendor acceptance rate*
75+%
Time reduction assessing vendors*
Automate. Collaborate. Validate.
Monitor vendor risk from procurement to reassessments to offboarding. With a customized approach to match the organization’s risk tolerance and program maturity, third-party risk management teams can combine workflow automation with objective data when evaluating vendors. Now that’s strategic decision-making.
We save hundreds of hours annually by using Bitsight. We’ve integrated Bitsight Vendor Risk Management into our onboarding and evaluation process, and it’s helped us identify the actual risk level associated with vendors.”
Simplified vendor risk management—at scale.
- Customized VRM Assessments
- Data & System Integrations
- Simplified Vendor Scoring
- Centralized Repository
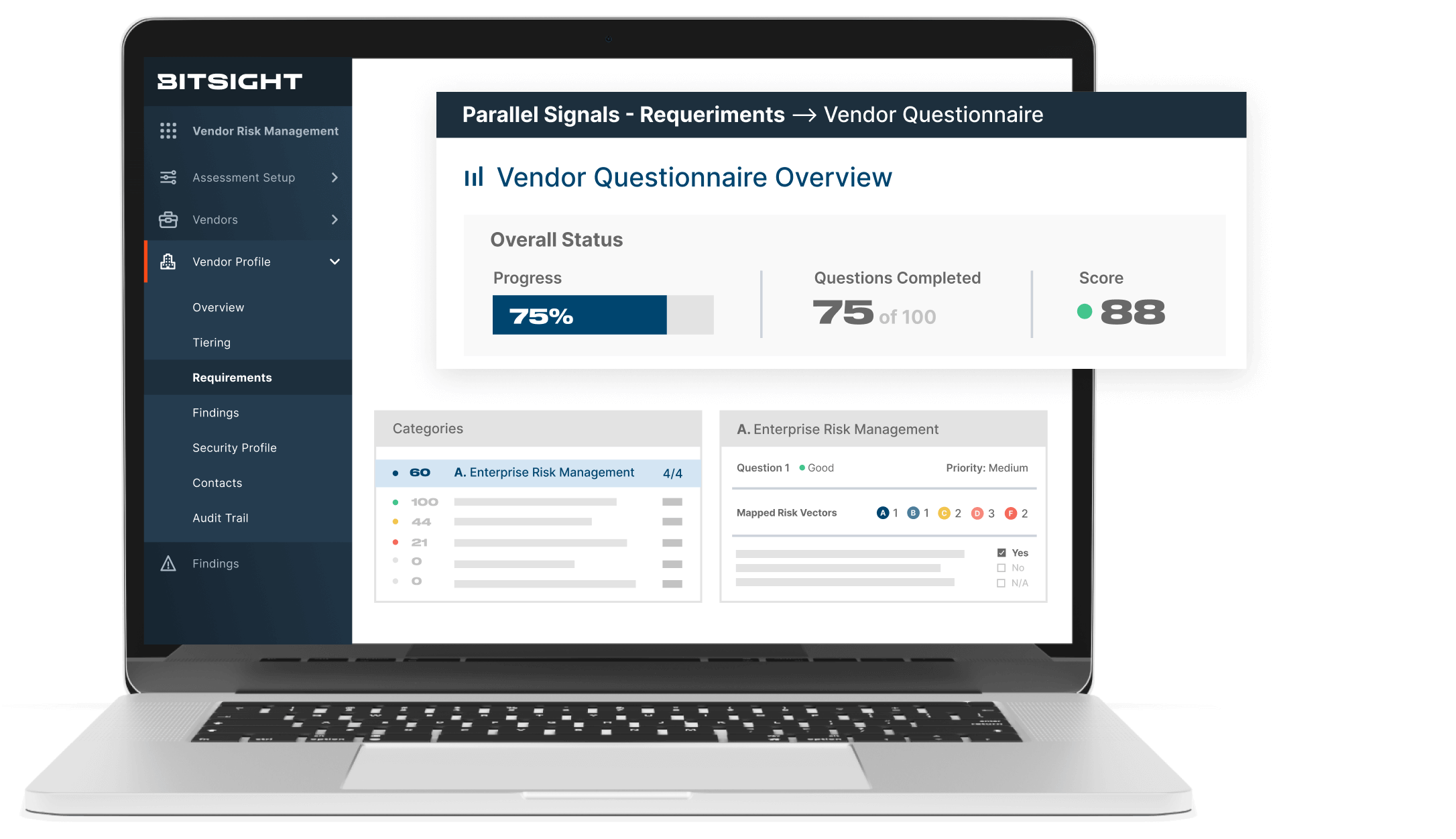
Tailor requirements based on criticality
No more chasing vendors through emails and spreadsheets. No more overly strict or lax requirements. Manage hundreds of third parties as effectively as you manage ten by focusing on the highest risks.
- Build sets of questions for different vendor tiers
- Only ask for what you need—no more, no less
- Gain insight from over 40,000 vendor profiles
Integrate your stack and share data across applications
Questionnaires are subjective. Complement them with objective data, fueled by Bitsight analytics and integrated data feeds. Make that data flow across your business tools to bring different programs together.
- Validate vendor responses with Bitsight risk vectors
- Gauge financial, geopolitical, and credential exposure risk with integrated external data feeds
- Sync VRM data with GRC and reporting tools through open API
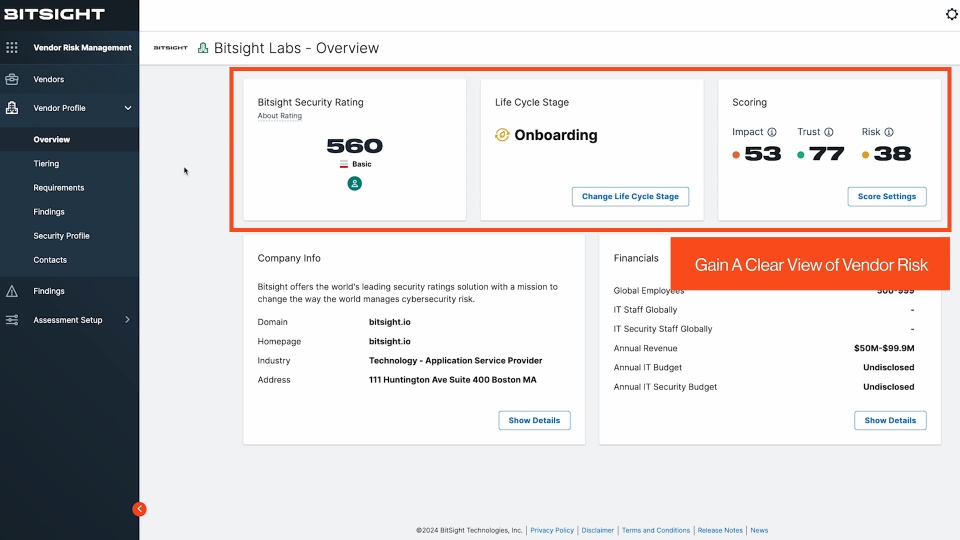
Understand risk to make informed decisions
A scoring system that combines pre-built metrics with your custom parameters to give the unknown a number—objectively measuring third-party security performance and impact to the organization.
- Impact Score: Measures inherent risk—the level of raw or untreated risk.
- Trust Score: Measures the trustworthiness of a vendor based on attributes that make for a strong security posture.
- Risk Score: Measures residual risk—the total risk of a vendor after implementing security controls—combining Impact and Trust scores.
Consolidate your vendor portfolio and interactions in one place
There are hundreds or thousands of third-party vendors in your ecosystem. But only one tool has the power to manage them all. VRM is your all-in-one vendor dashboard and audit trail.
- Automatically collect vendor data for audit purposes
- Build your single source of truth for risk assessments
- Increase VRM visibility and communicate wins easily
Resources
*As reported by existing Bitsight customers. Actual outcomes will depend upon a variety of factors unique to each customer and are not guaranteed.



