Singularity Control
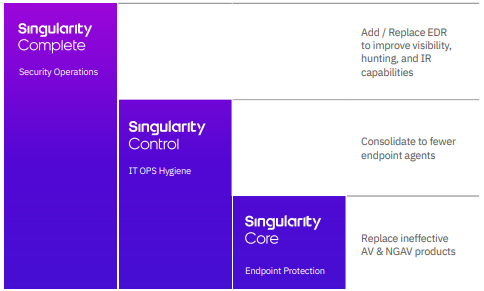
Singularity Control: The suite features you need. Made for organizations seeking the best-of-breed cybersecurity with additional suite features.
More capability. Same agent.
ORGANIZATIONS EXPECT OPTIONS FOR CONTROLLING THEIR DEVICES; SINGULARITY CONTROL ADDS HOLISTIC SUITE MANAGEMENT FEATURES.
CONTROL NETWORK FLOWS
Native OS firewall control for Windows, Mac, and Linux enables granular, location aware network flow control.
CONTROL USB & BLUETOOTH®
Control any USB, Bluetooth, or Bluetooth Low Energy device on Windows and Mac to reduce the physical attack surface.
ENSURE 100% DEPLOYMENT
Identify unprotected devices automatically to ensure compliance with security KPIs.
Network Control
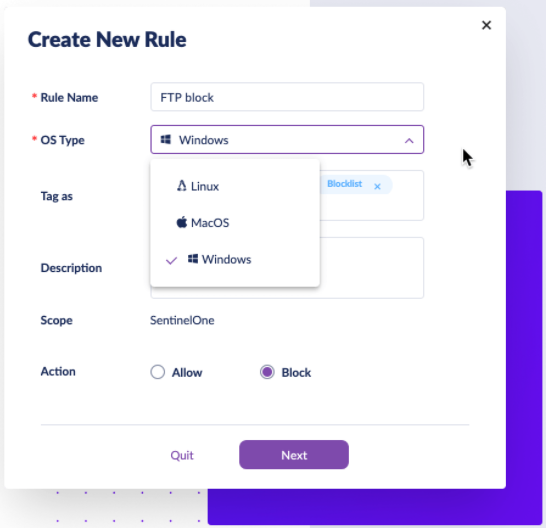
- Control inbound and outbound network traffic for Windows, Mac, and Linux.
- Centralized and customizable policy-based control with hierarchy inheritance.
- Tagging mechanisms for streamlined policy assignment and administrative clarity.
- Touchless location awareness that dynamically assigns network control based on the system’s physical location.
Device Control
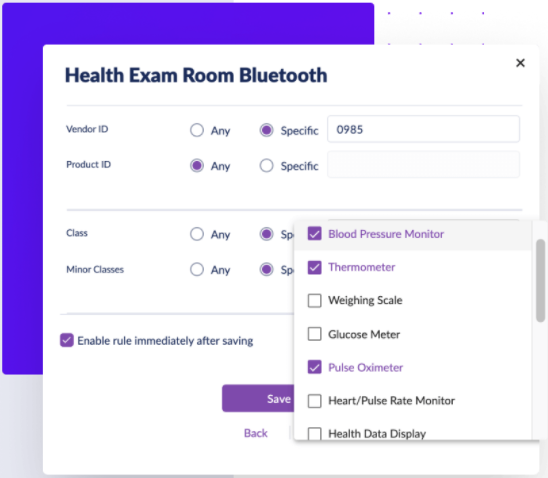
- Granular device control for USB and Bluetooth on Windows and Mac.
- Centralized and customizable policy-based control with hierarchy inheritance.
- Control any USB device type, not just mass storage, and specify full read-write or read-only operation.
- Control Bluetooth by protocol version and by specific Bluetooth device type.
- Control Bluetooth Low Energy devices.
Rogue Device Discovery
- The Rogues feature identifies the endpoints that are not yet protected by SentinelOne.
- Employs passive and active network sweeps to provide enterprise-wide visibility.
- Removes the uncertainty of whether or not your network is regulatory compliant by discovering deployment gaps.
- No additional software required.
- No network changes or hardware required.