Ransomware defense validation in-depth.
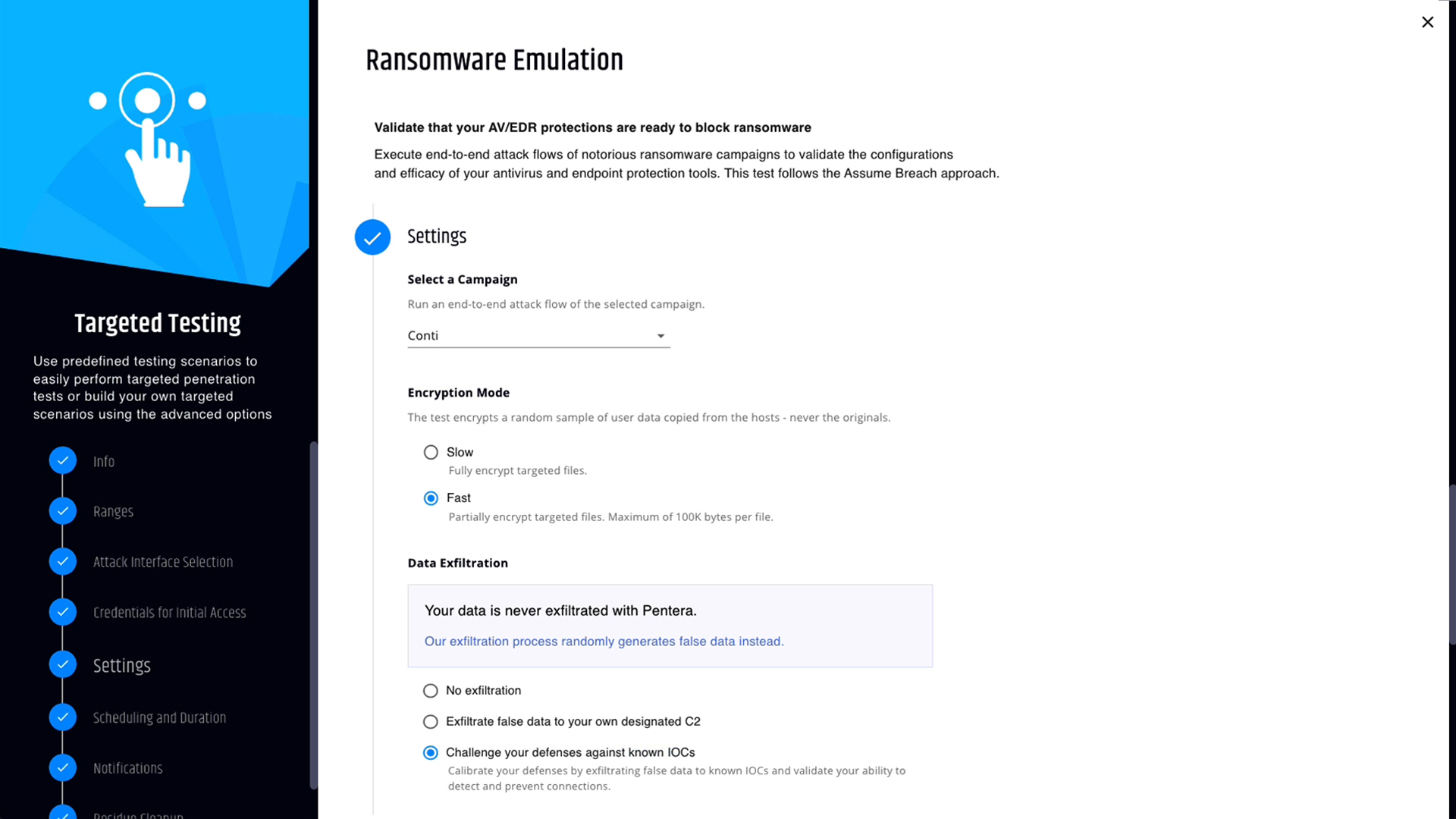
Emulate ransomware attacks
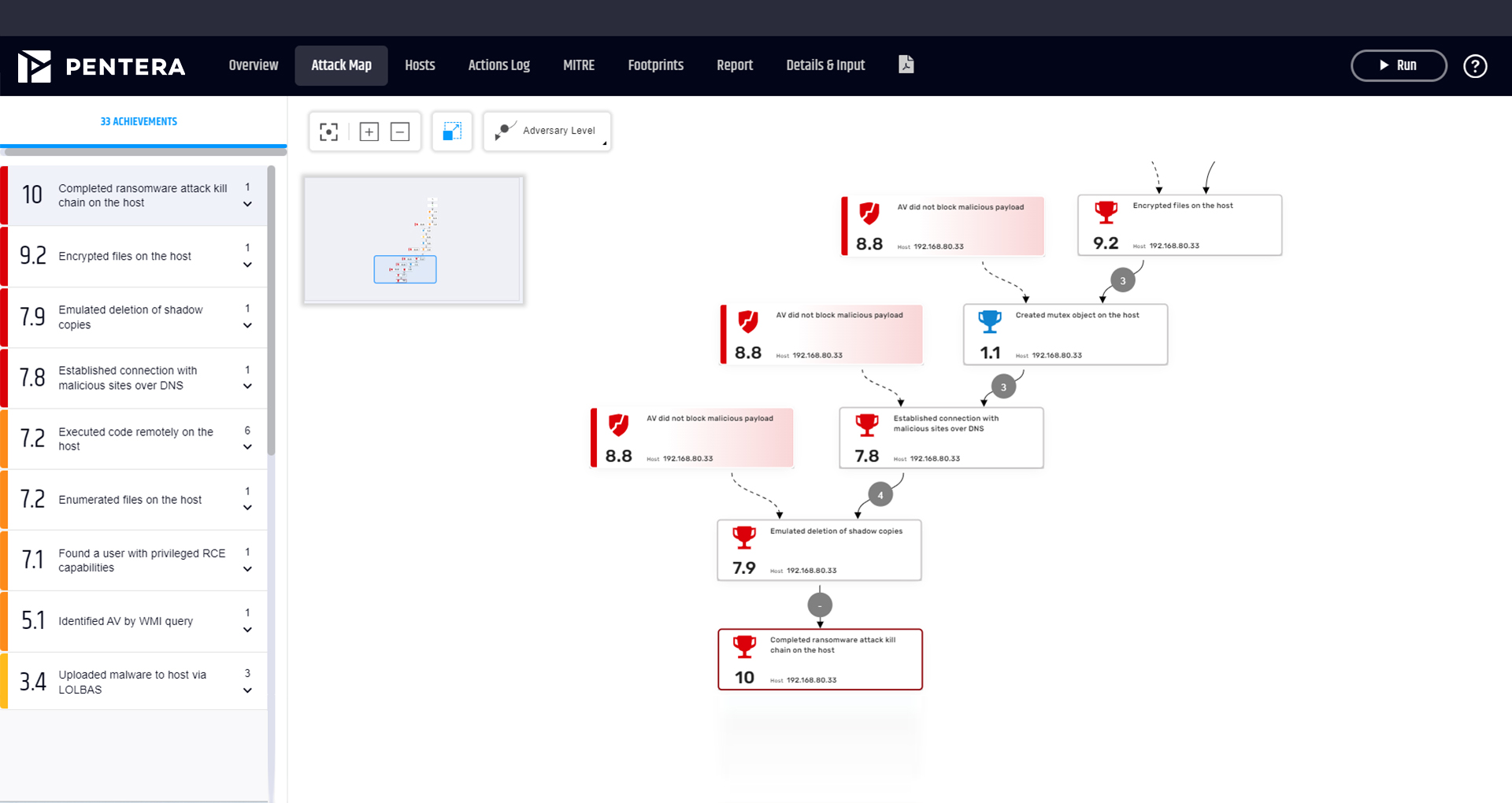
Apply safe versions of the most destructive ransomware strains found in the wild. Understand vulnerabilities and lateral pathways ransomware will take to target critical assets and disrupt your operations.
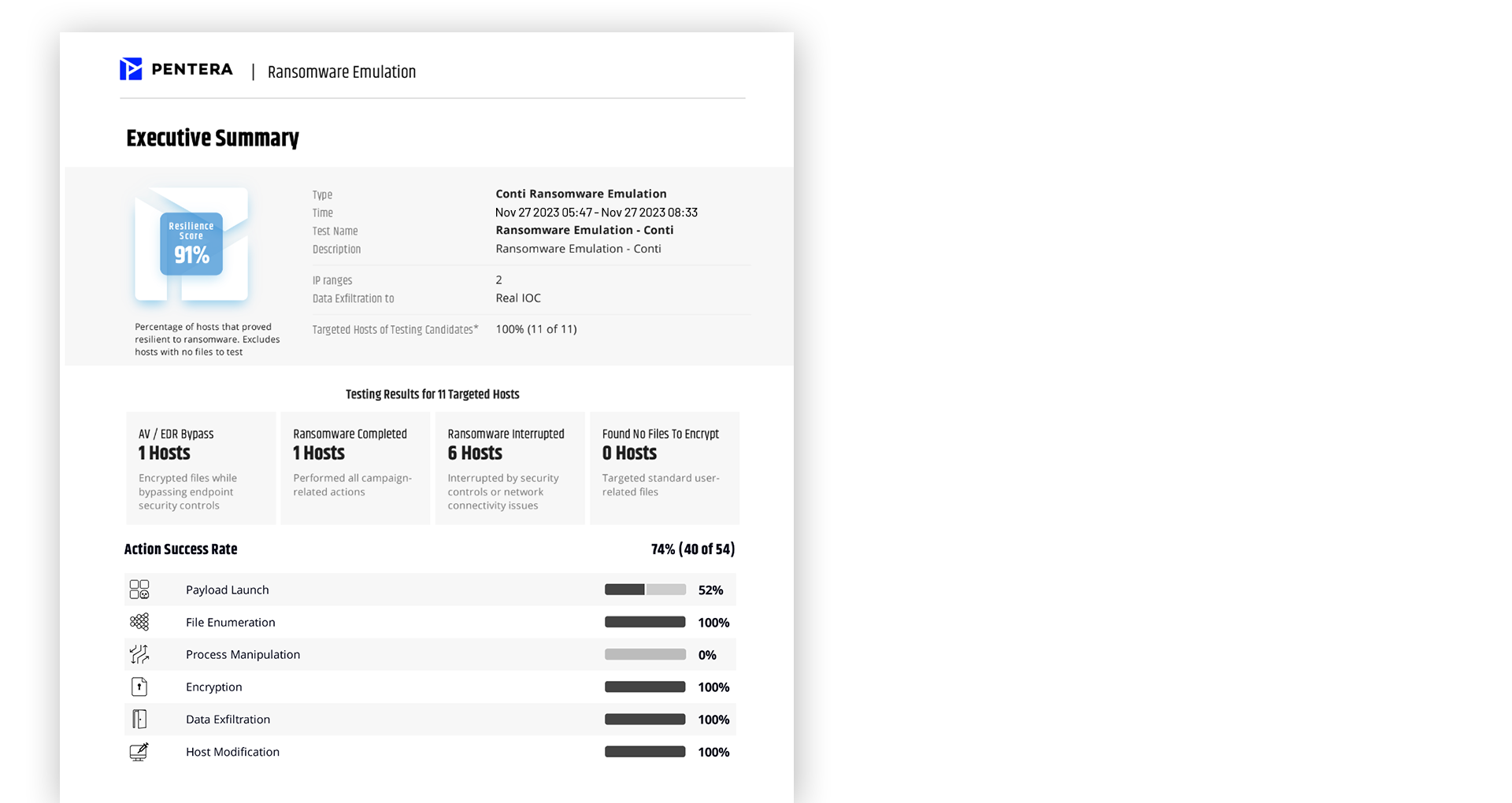
Validate endpoint protection efficacy
Launch initial exploitation, proprietary payload execution, encryption, and data exfiltration, all fully aligned to the MITRE ATT&CK® framework.
Mitigate ransomware risk
Follow the step-by-step remediation guide prioritized based on true risk to your business. Block attack paths and assure ransomware cannot propagate in your network.
Validate your entire attack
surface with the Pentera
Platform.
Fix the security gaps that really matter.

Your toolkit: Helpful resources for smarter security validation.
Find out for yourself.
Begin your security validation journey.



