External security validation in-depth.
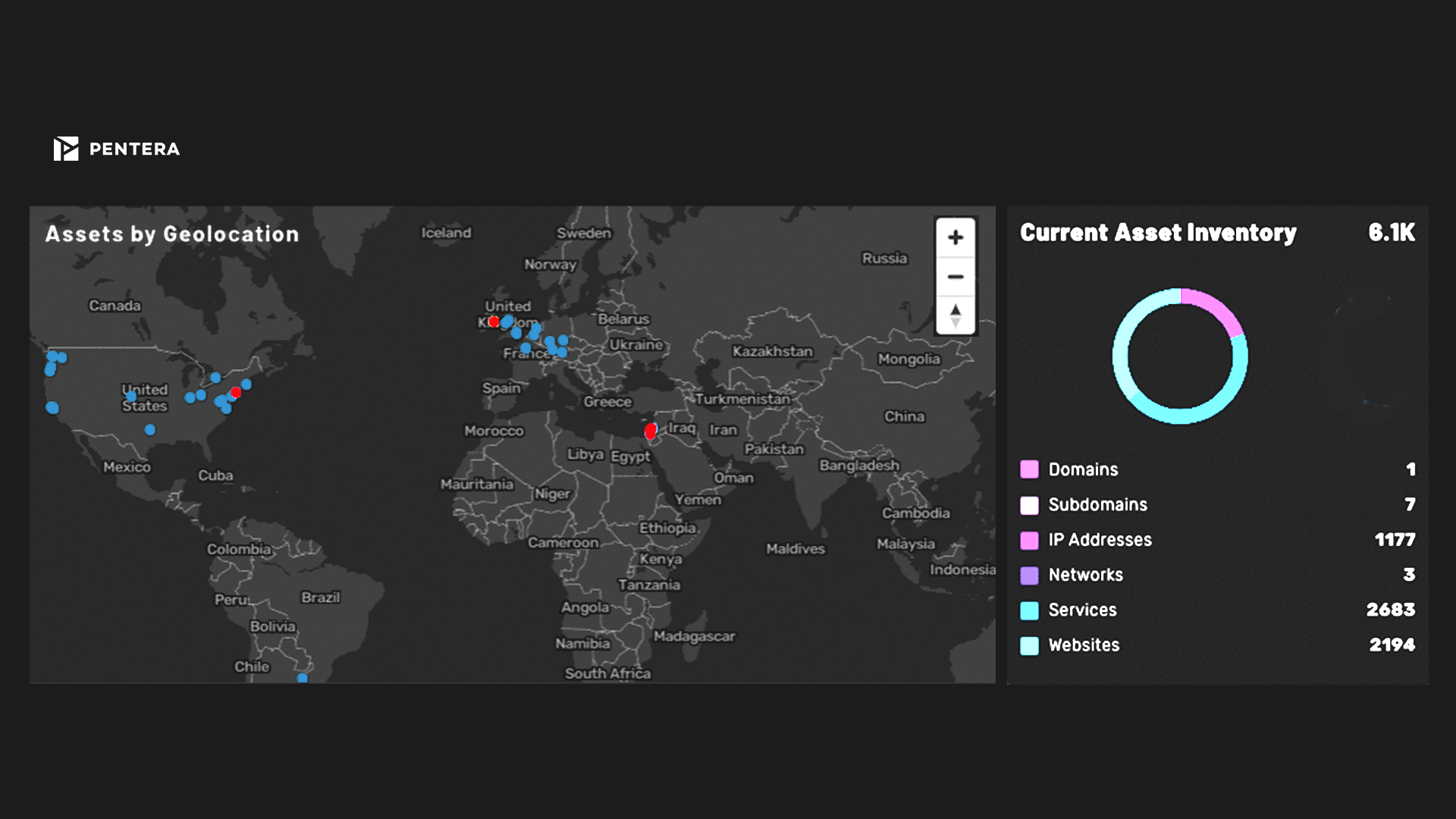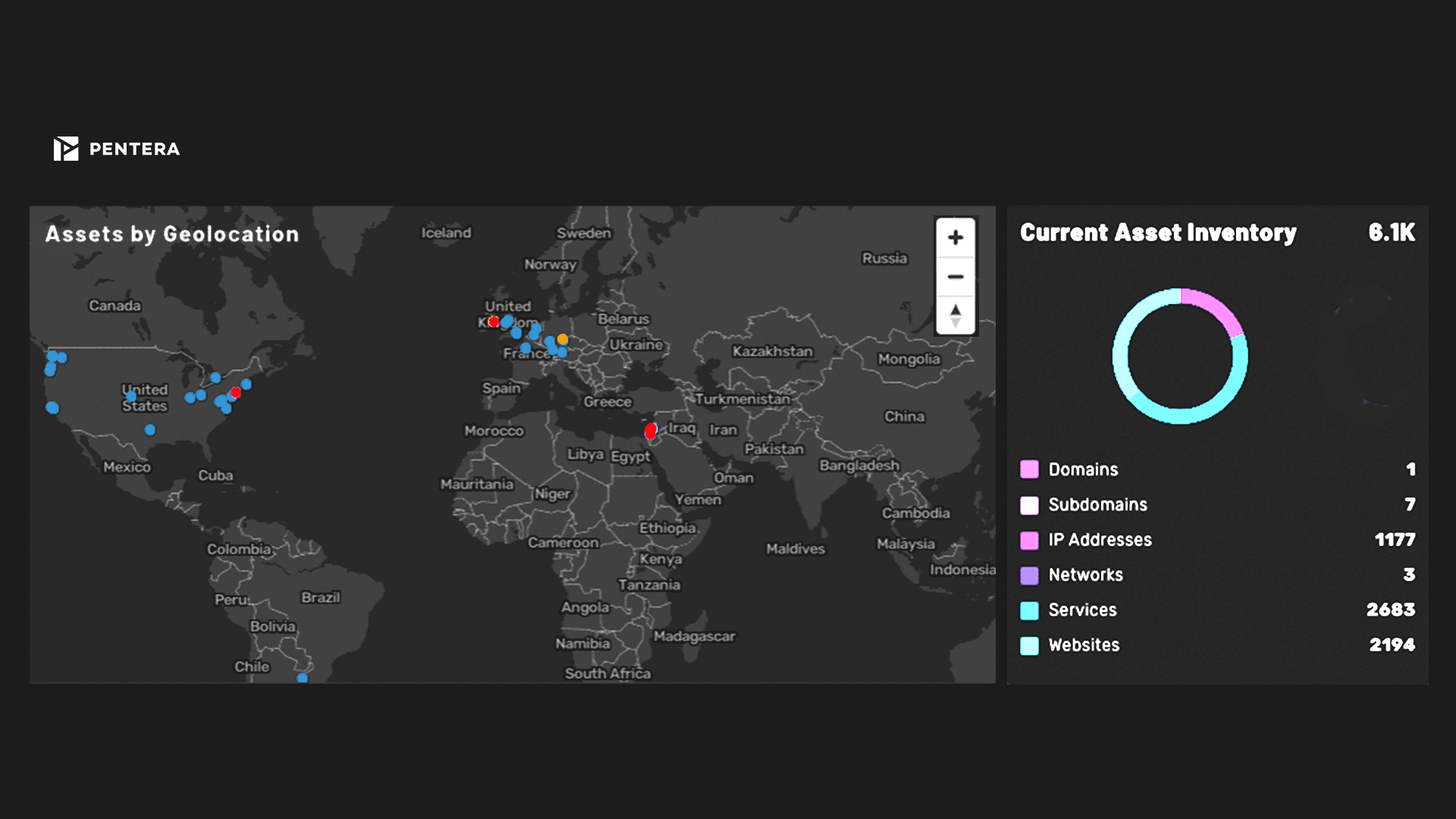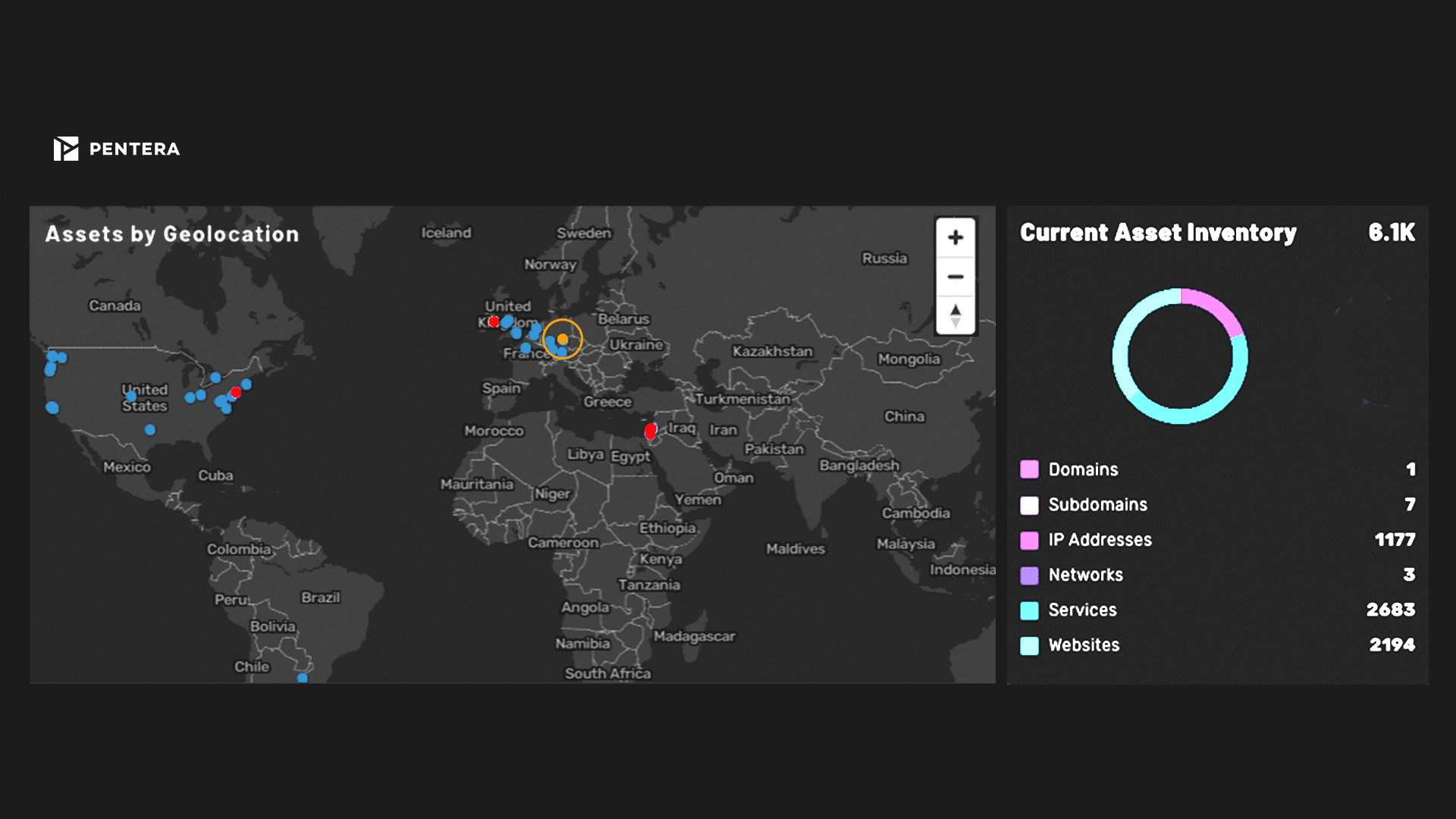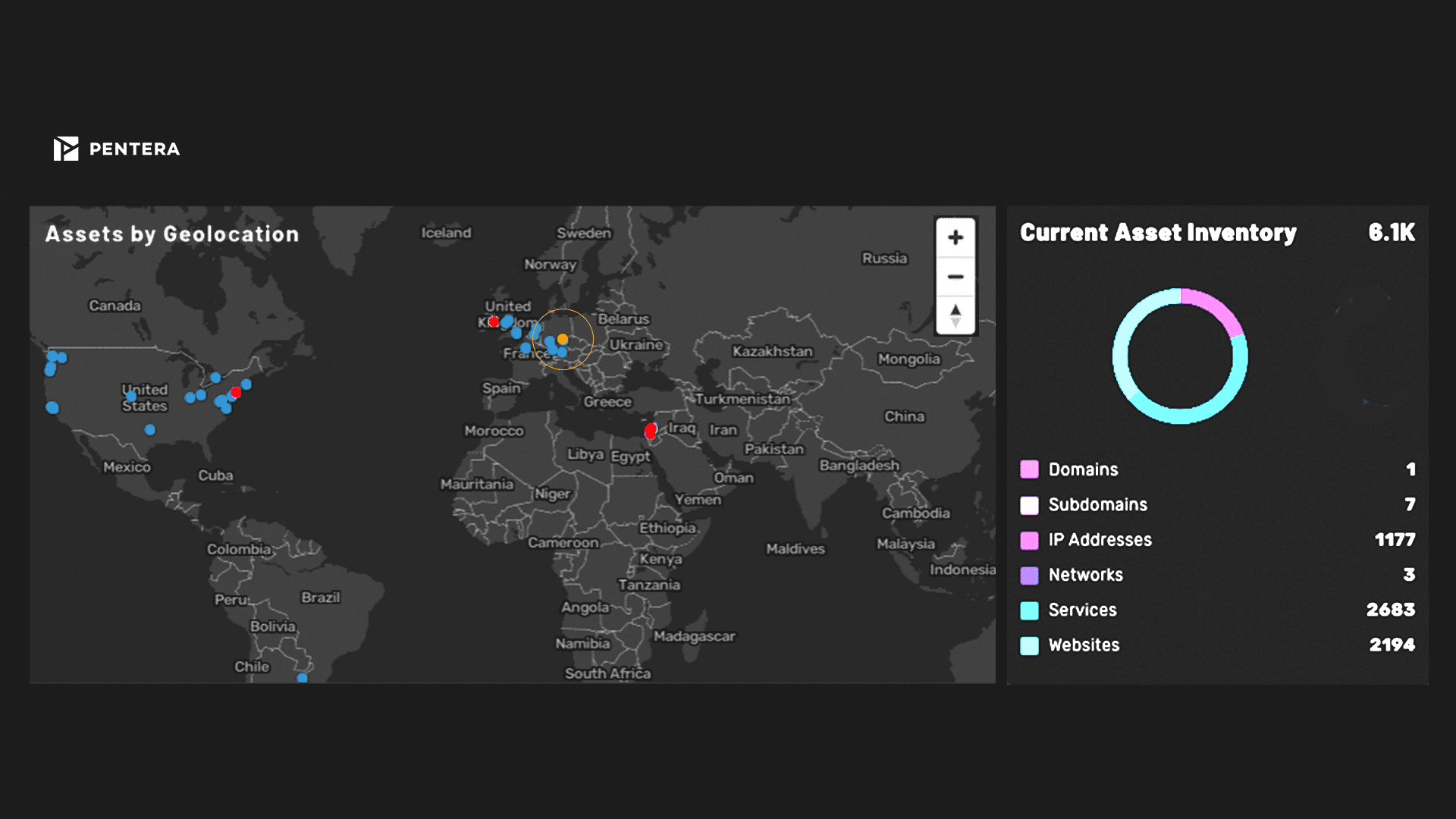
Continuous attack surface mapping and identification
Access our open-source intel (OSINT) to map your external attack surface through ongoing asset discovery and reconnaissance. Actively track and update your web-facing assets.
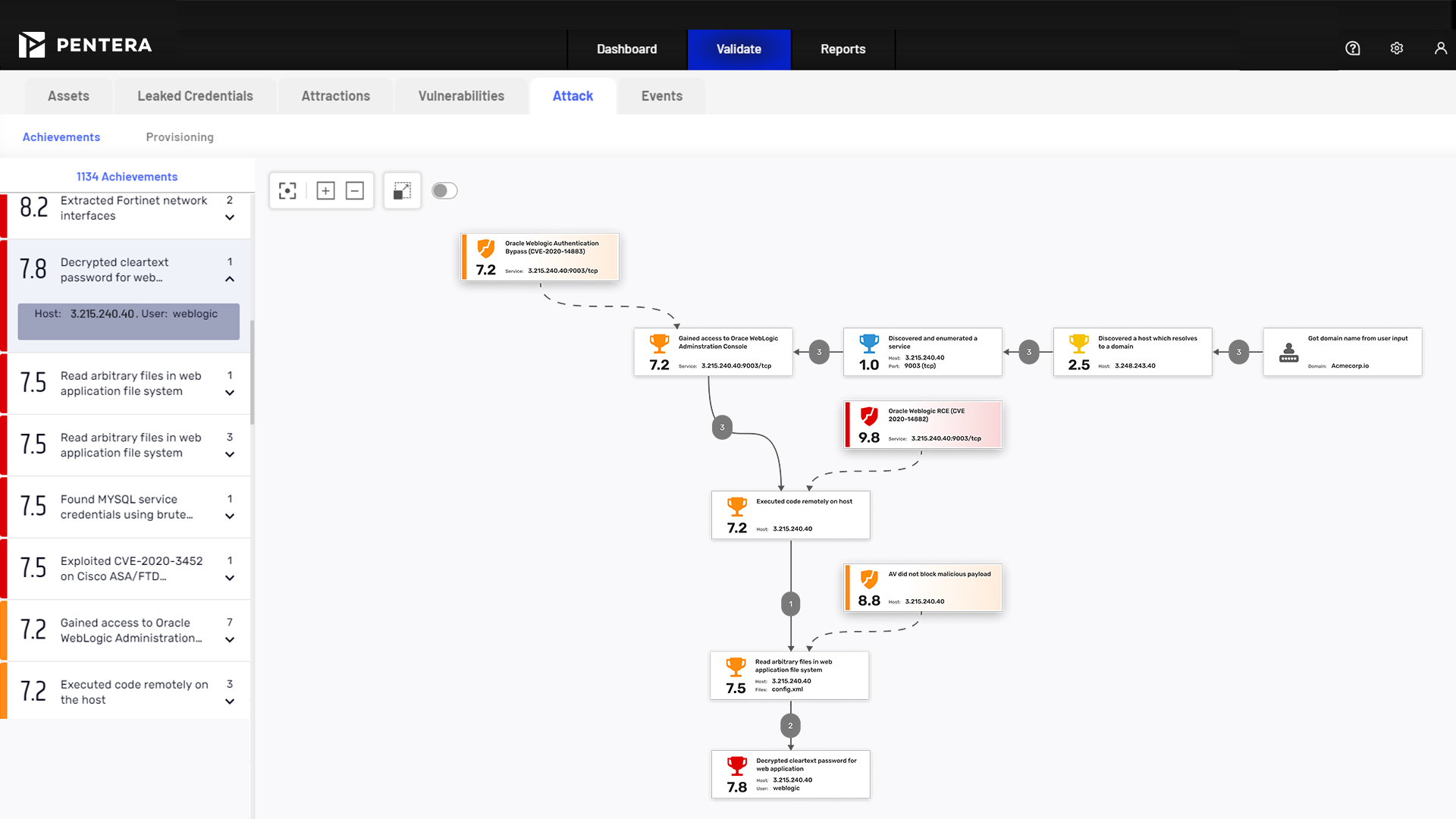
External attack path discovery
Launch safe-by-design attacks, aligned to OWASP and MITRE ATT&CK® frameworks, in order to understand the kill chain of your external assets.
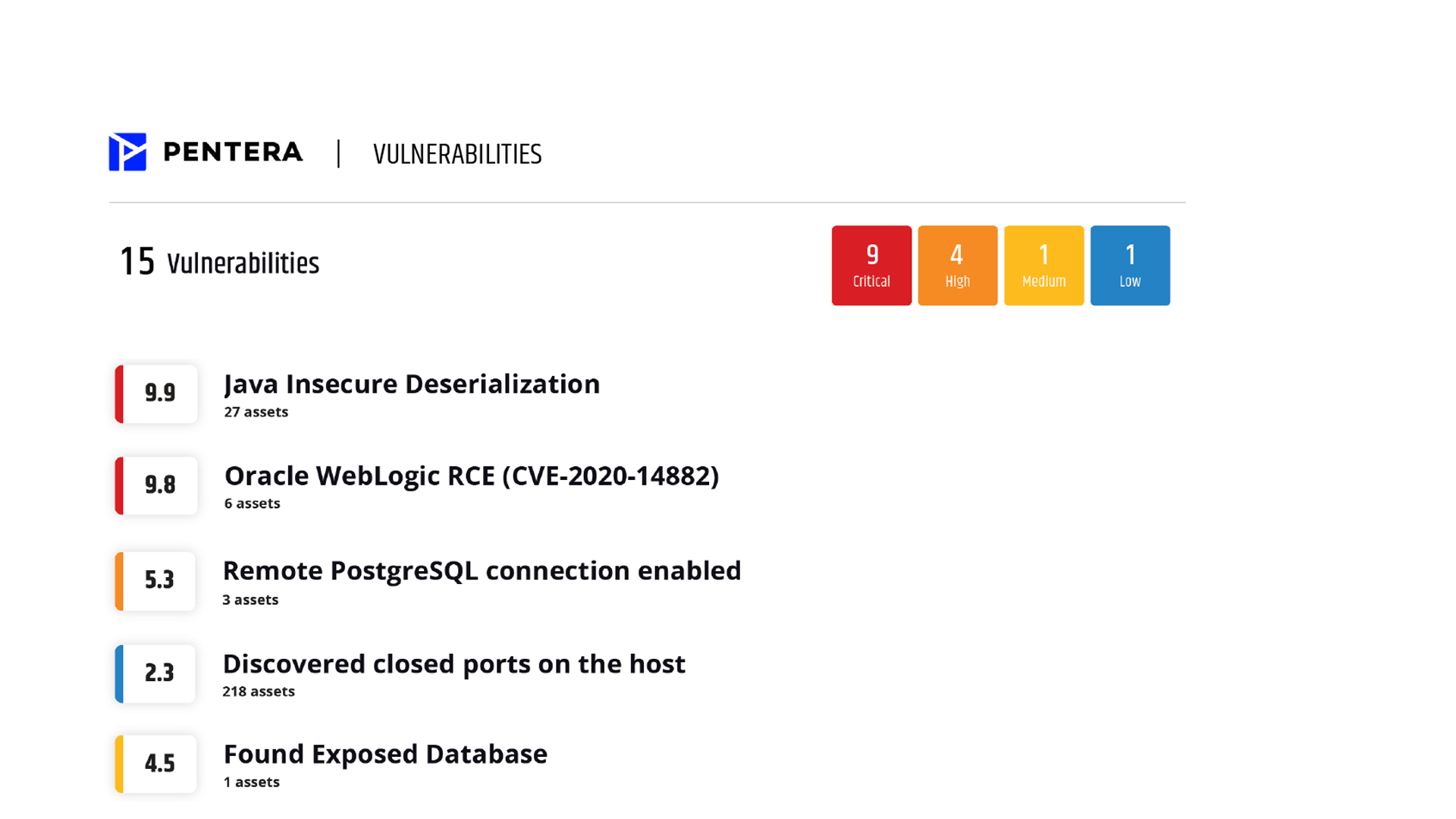
Prioritize exposure remediation
See your most attractive assets the way an adversary would see them. Focus your remediation efforts on the most exploitable security gaps based on potential risk to the business.
Validate your entire attack
surface with the Pentera
Platform.
Fix the security gaps that really matter.

Your toolkit: Helpful resources for smarter security validation.
Find out for yourself.
Begin your security validation journey.



