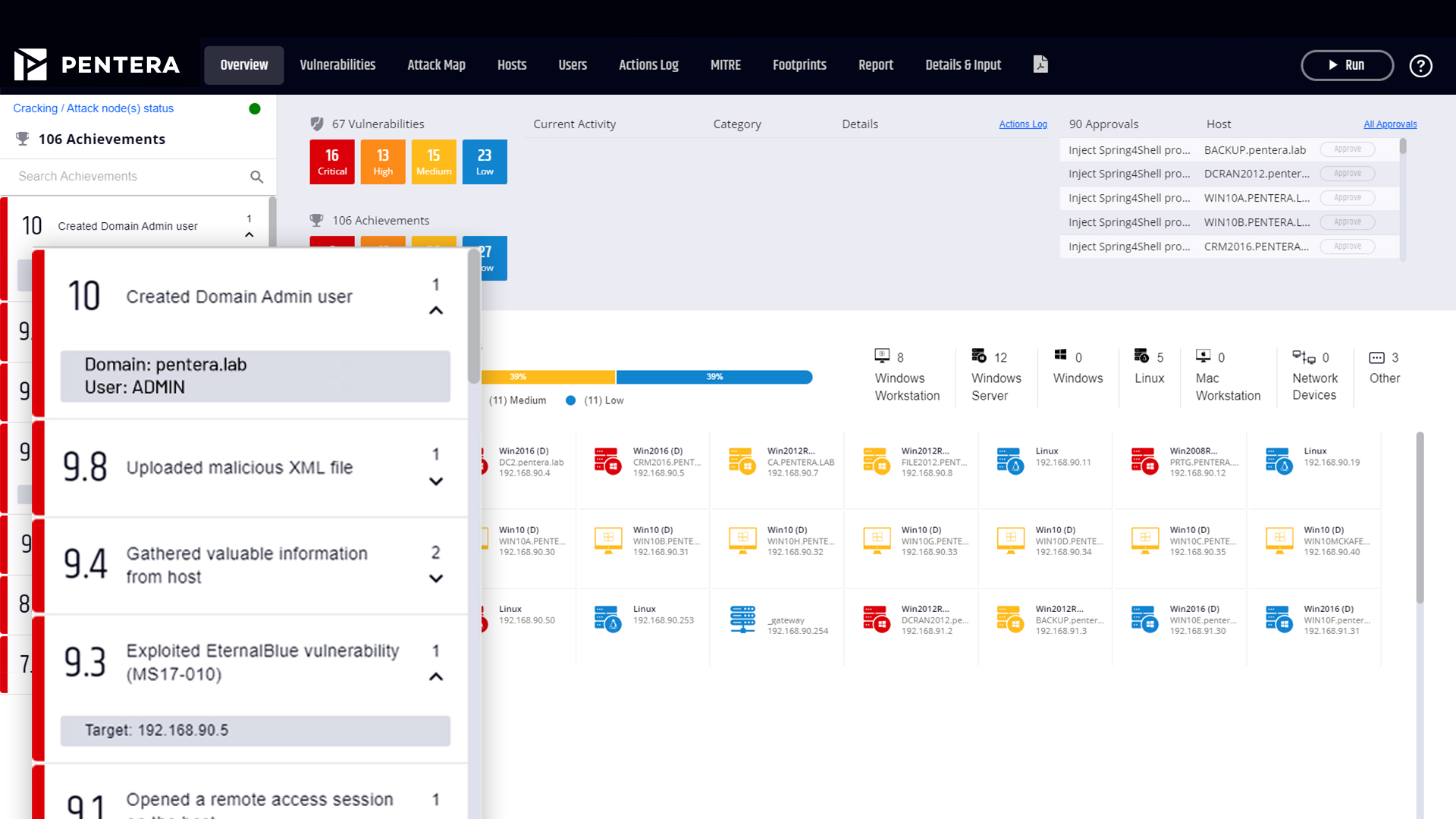
Network security validation in-depth.
Map your internal attack surface
Discover every corner of your internal network. Automatically gather information on users, hosts, networks, primary servers, and application configuration.
Challenge your internal controls
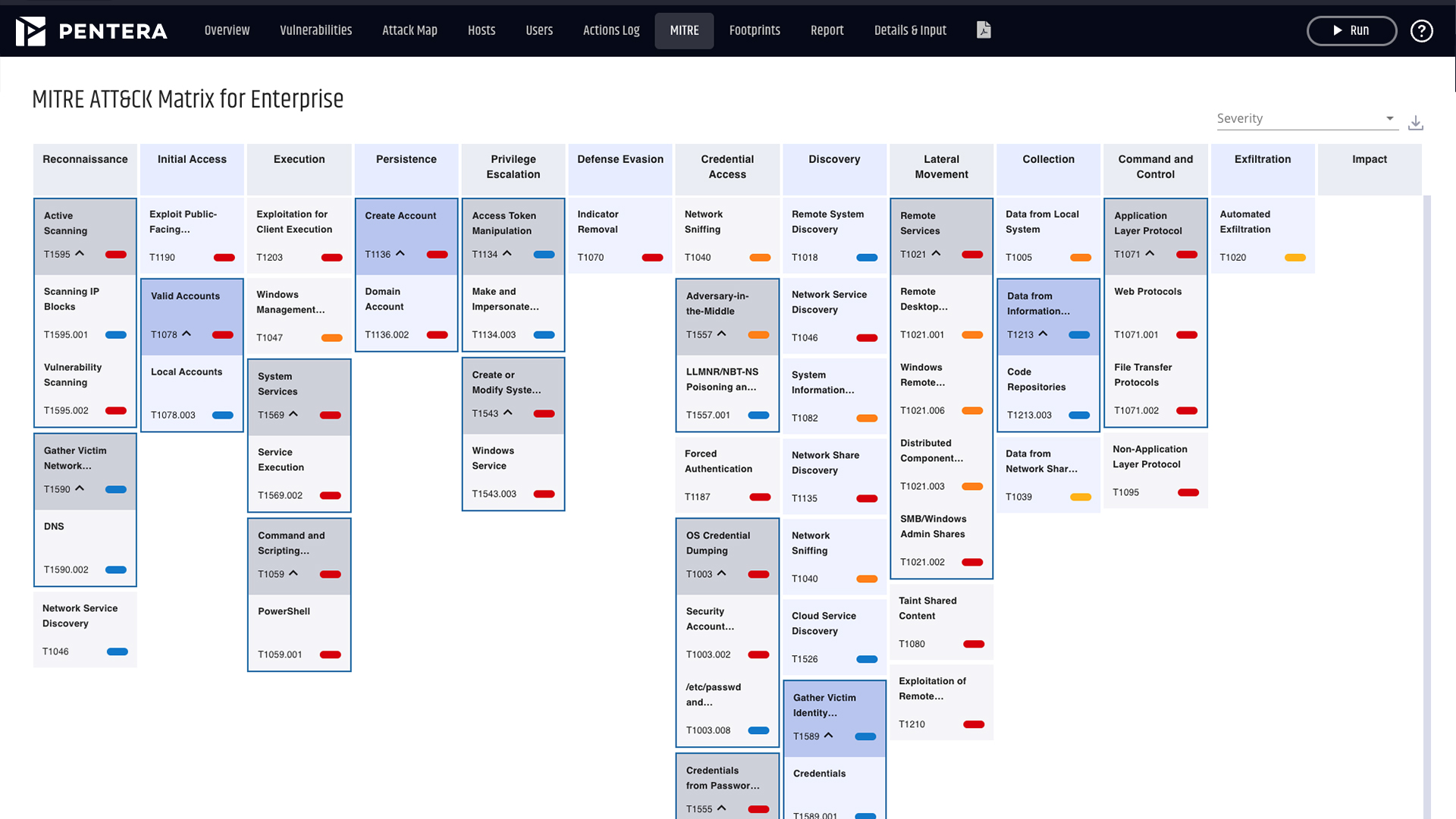
Apply our safe-by-design ethical hacking techniques. See the full attack kill chains, potential flaws, and vulnerabilities.
Prioritize exposure remediation
Reveal complete attack kill chains and pinpoint their root cause, so you can focus on what needs fixing first. Report progress and re-validate your security posture.

Validate your entire attack
surface with the Pentera
Platform.
Fix the security gaps that really matter.

Your toolkit: Helpful resources for smarter security validation.
Find out for yourself.
Begin your security validation journey.


