Log analytics and configuration management software
for network security devices

Firewall Policy Management
Analyze the usage and effectiveness of the Firewall rules and fine tune them for optimal performance.
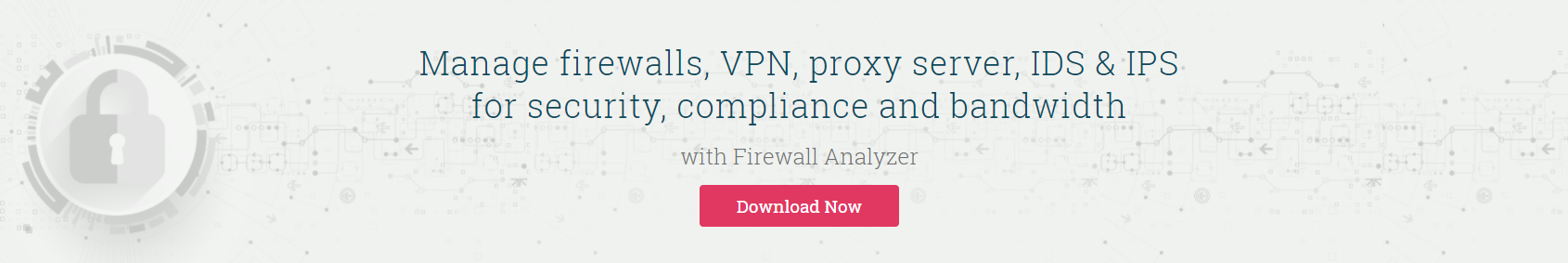
Change Management
Get instant notification about the changes made and get a complete trail of all the changes done to your firewall configuration with Change Management reports.

Network Security Management
Get detailed information on all possible network attacks and security breaches in your network.

User internet activity monitoring
Automatically identify users across various categories such as streaming videos, file sharing networks, social networks etc. This gives you greater visibility into the high risk users.
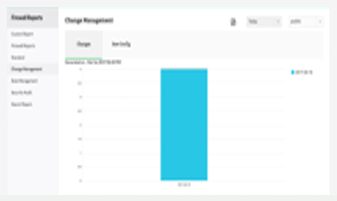
Real-time VPN and Proxy Server Monitoring
Obtain active VPN users, user-specific & user group specific VPN usage, sessions, and bandwidth consumed.

Compliance Management
Automate compliance audits with out-of-box reports and get your firewall security validated with security audit and device configuration analysis reports.
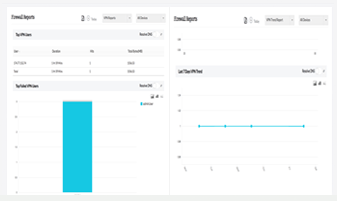
Network Forensic Audits
Search the logs and pinpoint the exact log entry which indicates the cause of the security event in minutes.

Log Analysis
Gain insight into security threat and traffic behaviour to improve the network security posture.

Network Traffic and Bandwidth Monitoring
Perform network behavioral analysis by monitoring for sudden spikes in bandwidth consumption and get in-depth details about users.
Why Choose Firewall Analyzer
Unlock the real value of your security devices
- Supports an extensive array of perimeter security device logs which include firewalls, VPNs, IDS/IPS and proxy servers
- Provides a wide range of reports for external threat monitoring, change management and regulatory compliance
Attractive TCO and rapid ROI
- No additional hardware required, minimal entry cost and maintenance inclusive subscription model ensures a low TCO
- Competitively priced. Quick deployment, instant results, reduced IT overhead ensures rapid ROI
Meet dynamic business needs quickly
- Rapidly transforms perimeter security device logs into actionable information
- Generates reports in user friendly formats like PDF and CSV formats
Productivity improvement for IT / MSSP
- From product deployment to report generation in minutes!
- Real-time alerts to security events enable IT to respond instantaneously to security threats
Try Firewall Analyzer For Free
- Access a single downloadable file for all three editions of Firewall Analyzer
- Get a link to the live online demo
- Get a link to the live online demo
Standard
Supports up to 60 Devices
Network Traffic Analysis
- Bandwidth Reports
- Inbound / Outbound Traffic
- Internet / Intranet Reports
- VPN Usage & Trend
- Protocol Usage
- Firewall Rules Report
- Sites Accessed by Users
- Firewall Device Audit Report
Network Security Reporting
- Attack / Virus Reports
- Spam Reports
- Failed LogOn Events
- Denied Events & Websites
- Insider Threat Reports
Dashboard
- Custom Dashboards
- User Specific Dashboards
Alert Management
- Criteria based Real-time Alert
- Network Behavioral Anomaly Alert
- Interface Bandwidth Utilization Alert
Forensic Analysis
- Incident Analysis with Raw data
- In-depth auditing with aggregated database entries
User Management
- Local Authentication
General
- Network Troubleshooting Tools
Professional
Supports up to 60 Devices
Firewall Rule Analysis
- Policy Overview
- Policy Optimization (Anomaly Detection)
- Rule Cleanup
- Rule Reorder & Recommendation
- New Rule Impact Analysis
Firewall Configuration Analysis
- Real-time Change Notification
- Historical Configuration Change Tracking
- Regulatory Compliance (ISO, PCI-DSS, NERC-CIP, SANS, NIST)
- Security Audit Report
- On-demand Configuration Backup
Dashboard
- NOC/SOC View
- Embed Widget
User Management
- AD Based Authentication
- Radius Authentication
- Pass Through Authentication
- REST API Access
General
- Rebranding
- Diagnose Connections
- Multi-Language Support
+ All the features of Standard Edition
Enterprise
Supports up to 1200 Devices
- Scalable architecture
- Monitors multi-geographical locations
- Distributed central-collector architecture
- Site specific reports
- Web-client Rebranding
- Client & user specific views
+ All the features of Professional Edition