Axonius Cybersecurity Asset Management
Axonius Cybersecurity Asset Management aggregates, normalizes, deduplicates, and correlates asset data from existing data sources to give customers a complete cyber asset inventory, uncover security issues, and automate remediation action — reducing the attack surface and simplifying workflows.
We don’t accept that reality — and neither should you. Axonius Cybersecurity Asset Management empowers you to get answers and trigger action, all within a unified view of your assets. As the system of record for all assets and infrastructure, Axonius gives you a true understanding of your environment at all times.
Comprehensive asset visibility
Get a comprehensive, always up-to-date asset inventory.
Security control coverage
Uncover gaps in security policies, configurations, and hygiene.
Automated policy enforcement
Automatically apply security policies to harden assets against attack.
Asset Data Enrichment
Gain rich context from internal and external sources to uncover risk.
AXONIUS CYBERSECURITY ASSET MANAGEMENT TOUR
Get a Complete Asset Inventory
With integrations to 800+ sources of business, IT, and security data — and without agents to install — the Axonius Platform inventories all your assets in a matter of hours, eliminating blind spots.
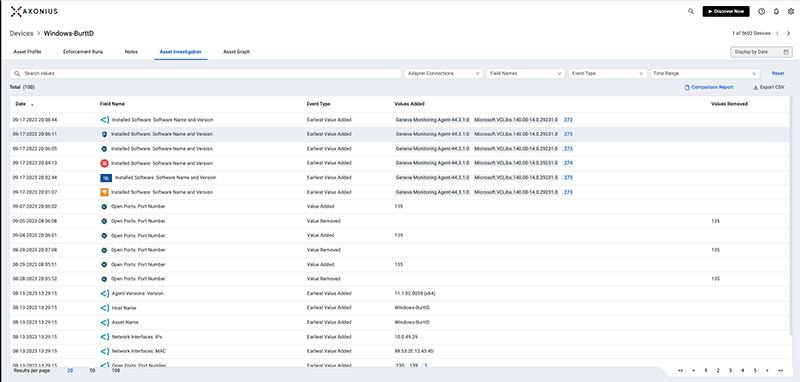
Identify Security Coverage Gaps
Use predefined or custom queries to discover how each asset stacks up against your cybersecurity policies and uncover risks and gaps.
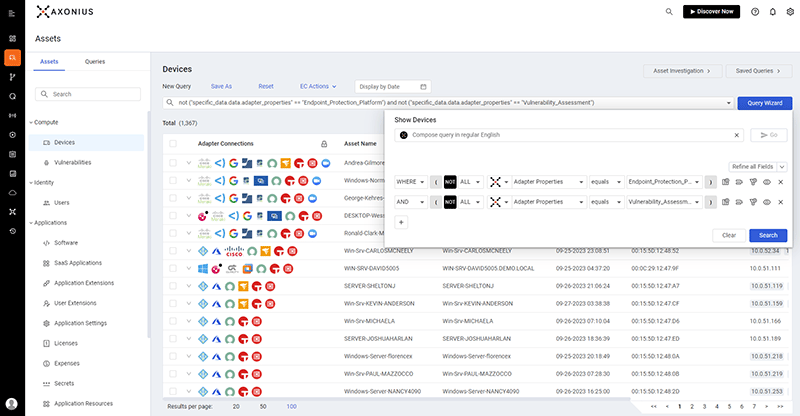
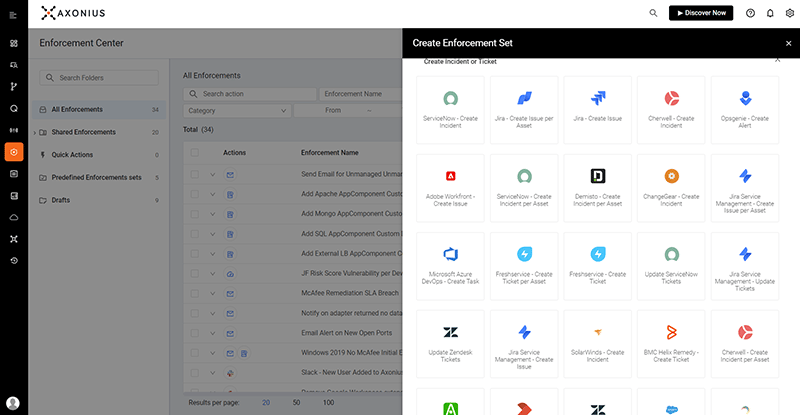
Validate and Automate Security Policies
Leverage custom enforcement sets, set triggers, and automate responses to optimize your security policy enforcement. Discover risky software, high-risk vulnerabilities, misconfigurations, and more.
WHY TEAMS TRUST AXONIUS
See the Platform
See the Axonius Platform for yourself with an interactive product tour, where we’ll guide you through key applications of our Cybersecurity Asset Management and SaaS Management solutions.
Book a Demo
Request a demo to learn how the Axonius Platform provides a system of record for all digital infrastructure helping IT and security teams manage an always-expanding sprawl of devices, users, software, SaaS applications, cloud services, and the tools used to manage and secure them.
