Cyber Security Assessment
Homepage/ IT Security Audit & Advisory / Cyber Security Assessment
A Cyber Security Assessment is performed to identify the current security posture of an information system or organization. The assessment provides recommendations for improvement, which allows the organization to a reach a security goal that mitigates risk, and also enables the organization.
FILE SERVER AUDIT
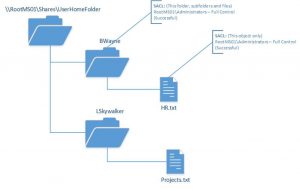
ACTIVE DIRECTORY AUDIT
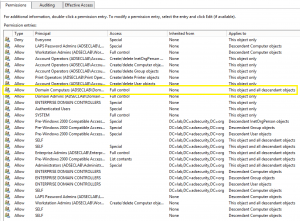
VULNERABILITY AUDIT
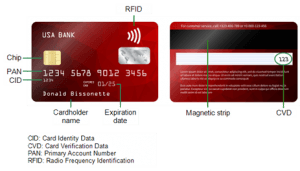
SENSITIVE DATA AUDIT
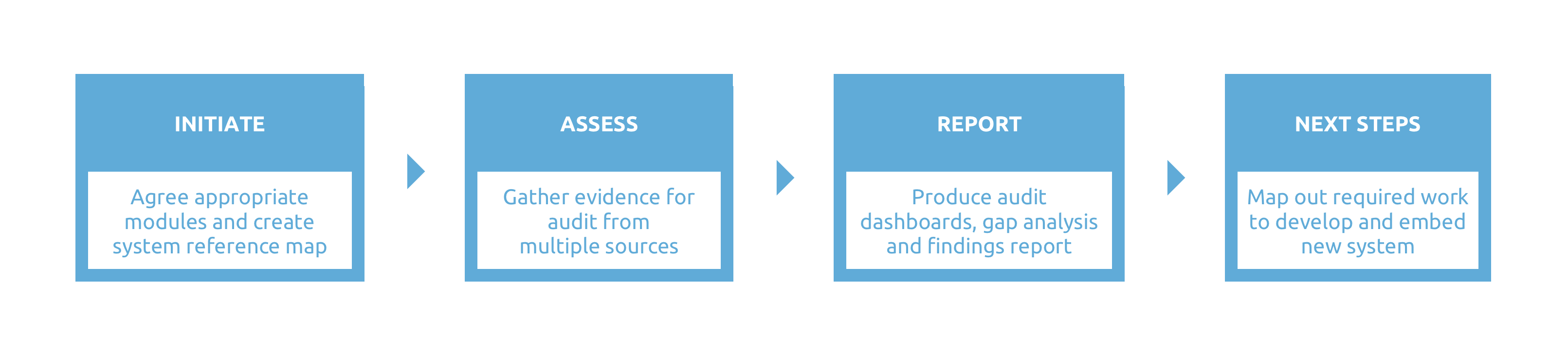
Stage 1: Initiate
We will work with you to understand your needs and agree the most appropriate elements of security management and duty of care to audit your organisation against. From this we develop a system map consisting of the 4 core modules – FILE SERVER AUDIT, ACTIVE DIRECTORY AUDIT, VULNERABILITY AUDIT & SENSITIVE DATA AUDIT
Note that the safeguarding and do no harm, wellbeing and resilience, and information security modules are high-level, security management related assessments, which will identify and trigger recommendations for dedicated audits in those areas if required.
Stage 2: Assess
We will gather evidence for the audit from several sources, including:
-
Document review (policies, handbooks, etc.)
-
Workshops with risk owners and risk managers
-
Interviews with key stakeholders, including those who are risk exposed as well as partners, funders and other relevant parties
Stage 3: Report
We will provide you with a detailed findings report and gap analysis, including summary audit report dashboards for intent and implementation based on the agreed system reference map.
We will clearly explain in non-technical language the changes that your organisation should make in order to meet the standards that we are auditing you against. This will include recommendations for policies and procedures, further audits, and staff trainings. We will also include a summary of the key threats and opportunities that your organisation faces with regards security management and duty of care as well as recognise those areas where your organisation is doing well.
Stage 4: Next steps
We will work with you to map out the next stages of developing a revised security risk management framework for your organisation and embedding it within your working practices and staff team. We can also provide additional support, such as a crisis management simulation, a retained security risk management consultant or ongoing training to ensure that your organisation stays secure and continues to meet its duty of care obligations.
A security audit can take from a minimum 2 days (Quick Assessment) and will usually take several weeks to complete, but it varies depending on the size and complexity of the organisation being audited.
Step 1: CONTACT
Reach out so we can scope the work. ->
Step 2: DIAGNOSE
We send you a free diagnose plan and Quote
Step 3: AUDIT
We Audit all the objects of the required scope
Step 4: IMPROVE
Your team fixes the problems.
We are also always available for advisory and consultancy.
Step 5: RE-AUDIT / CHECK-UP
We Audit your objects of the required scope again to see what has been improved.

Try Cyber Security Assessment For Free
- Access a single downloadable file for all 3 editions of ServiceDesk Plus on Windows or Linux machines
- Get a link to the live online demo
- Schedule a personalised one-to-one demo with one of our Product Experts
More Info
Office Hours: 9:00 – 18:00
Email: sales@sertalink.com
Phone: 32(0)3.337.17.01
