Check and eliminate compromised credential threats safely.
Use the latest credential threat intelligence
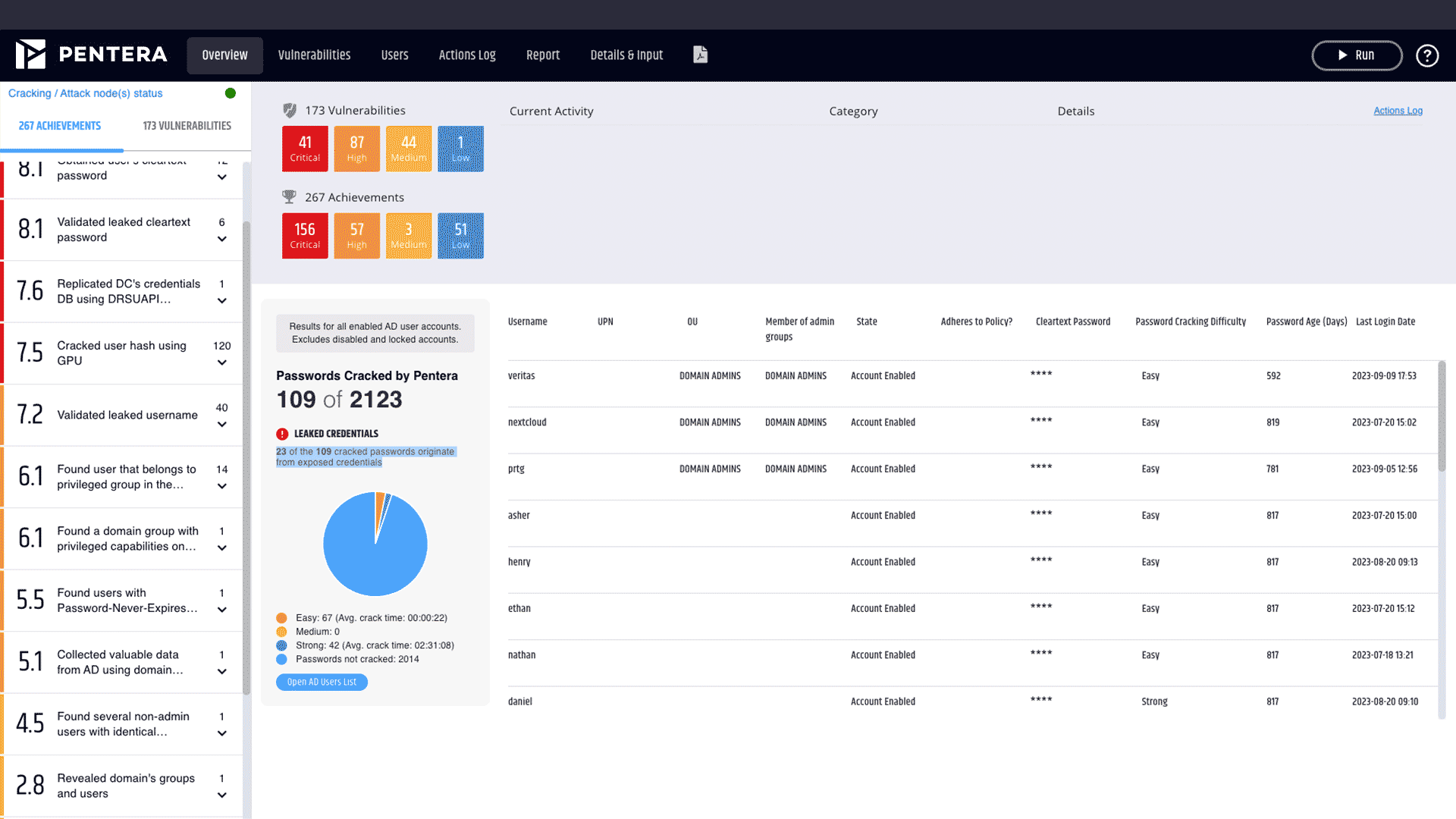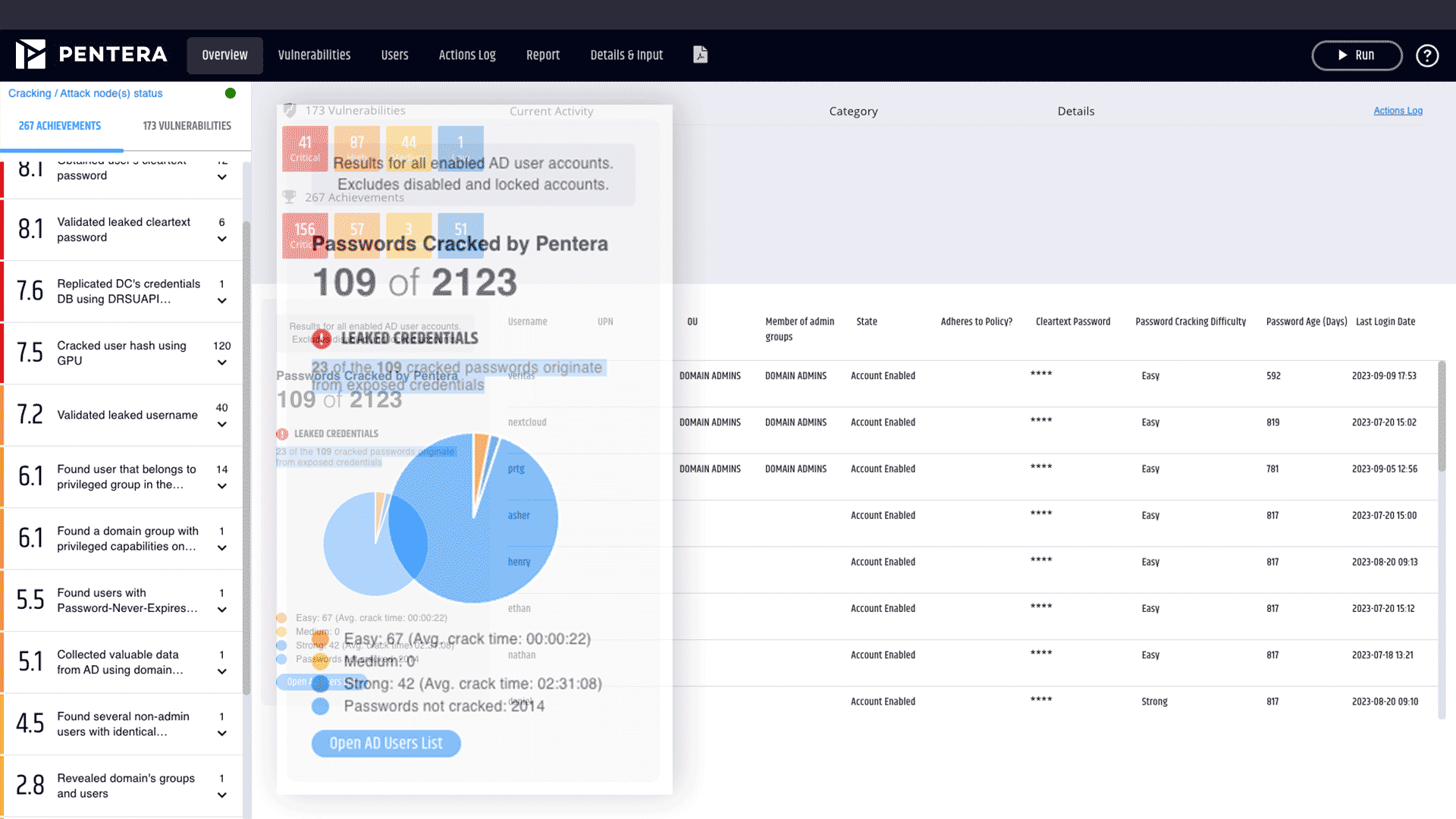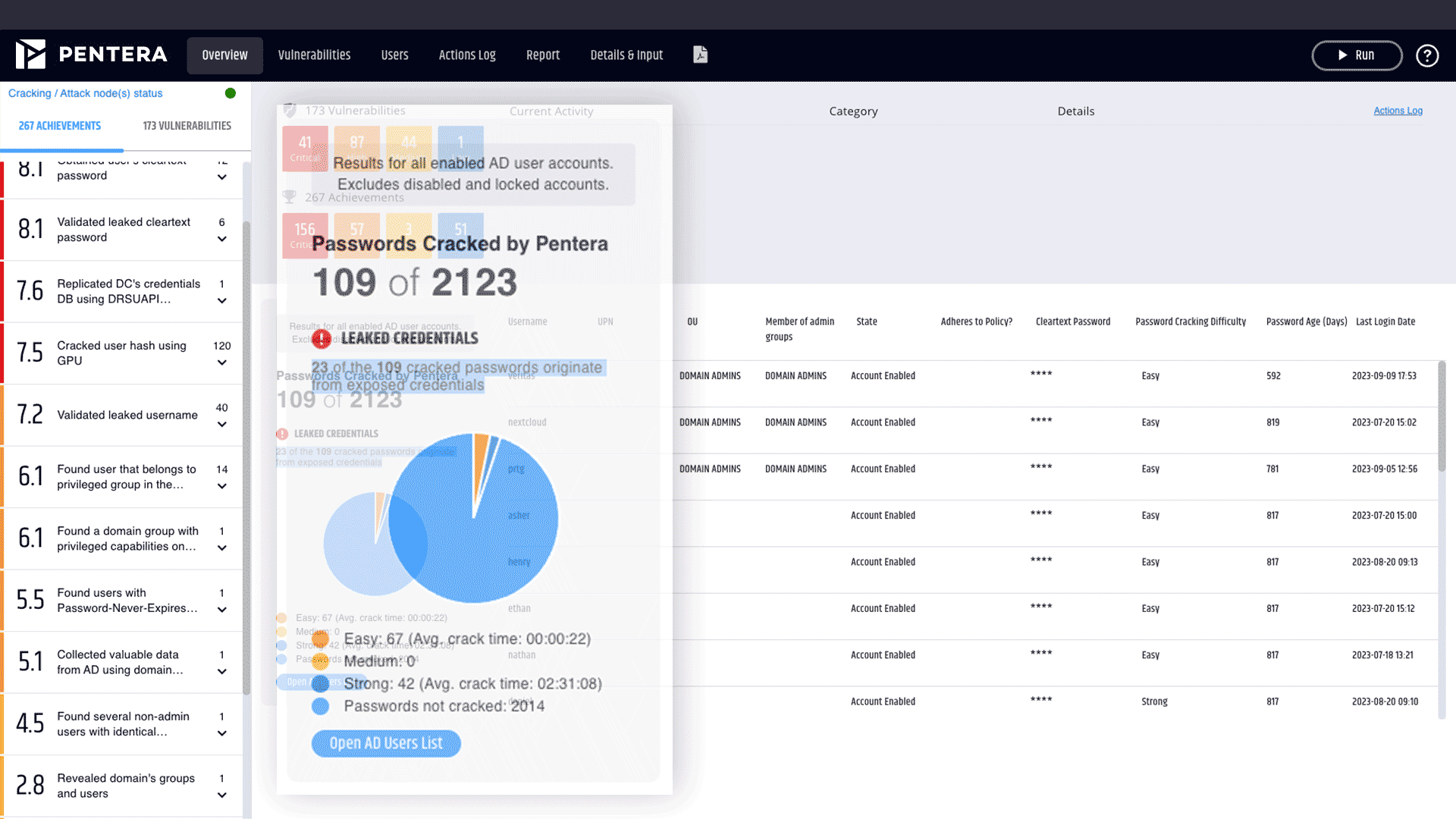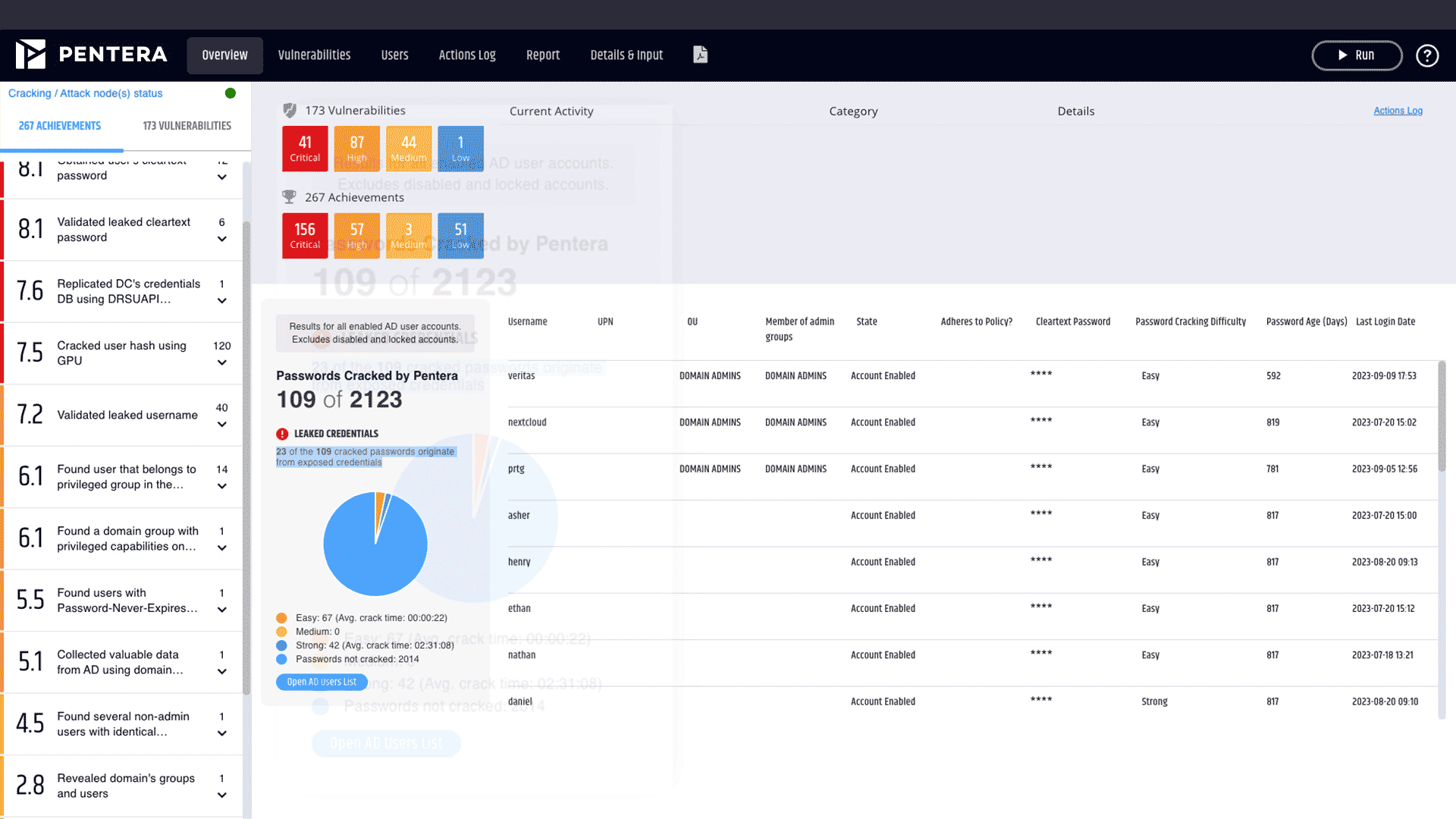
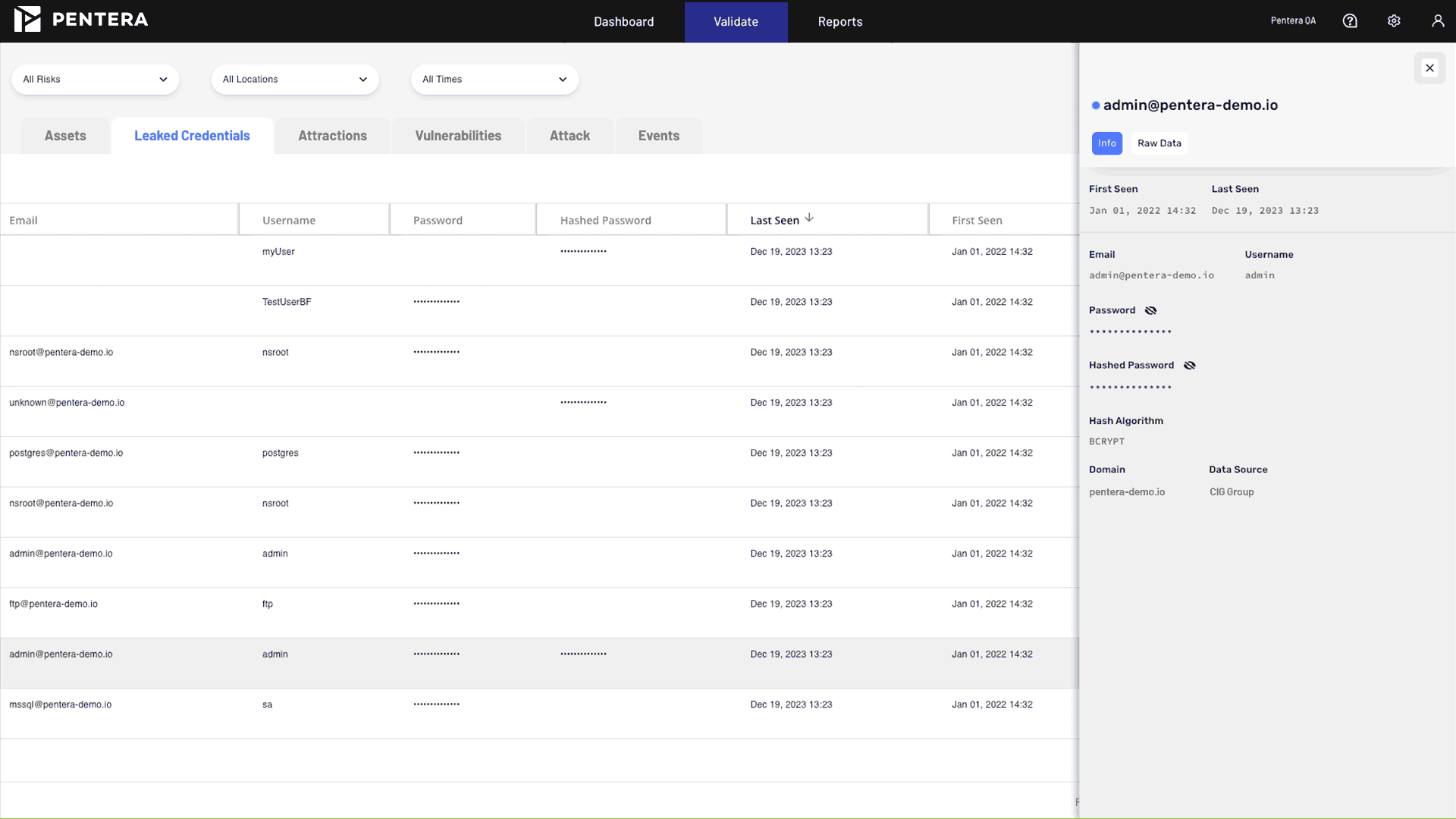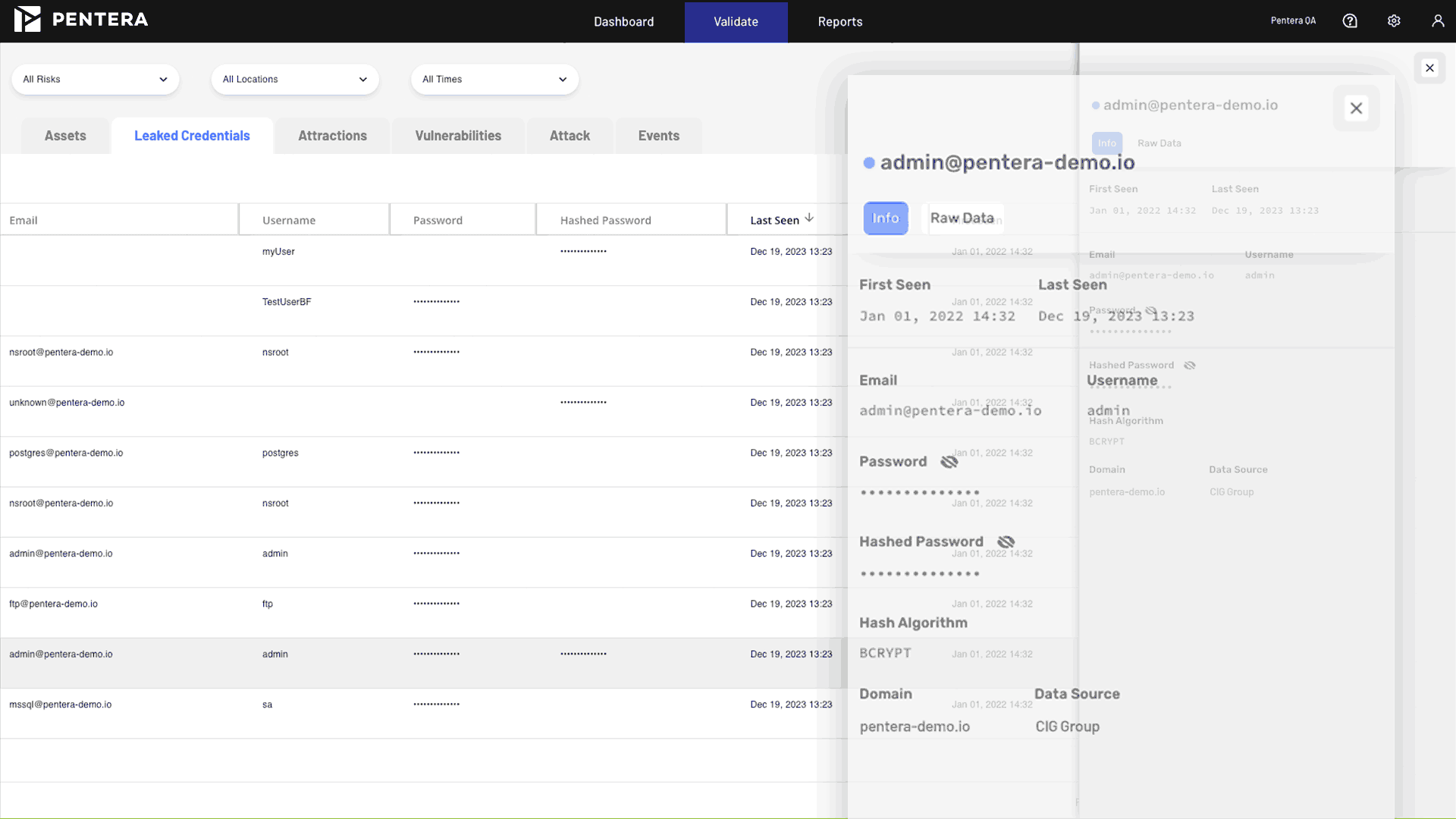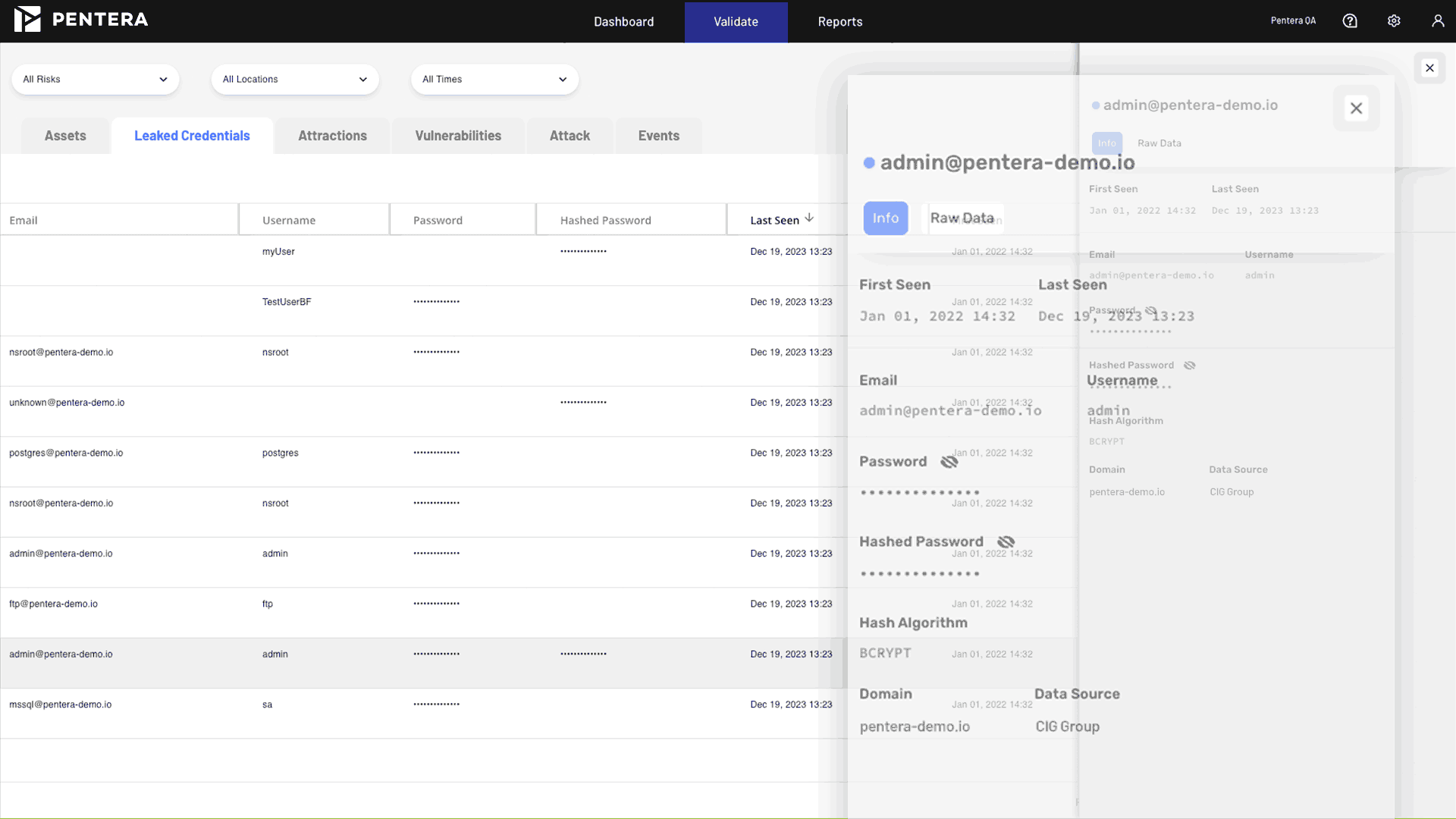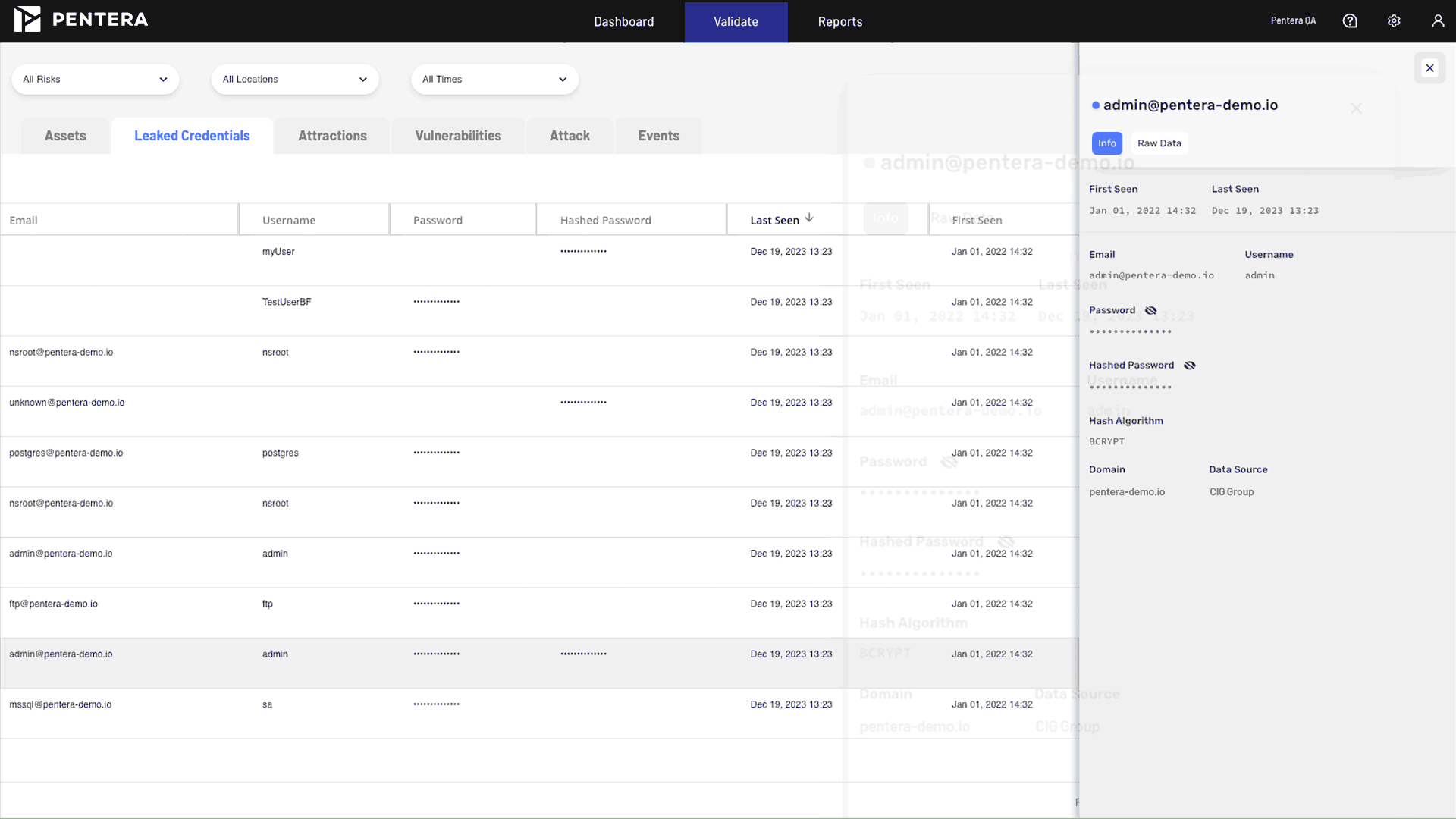
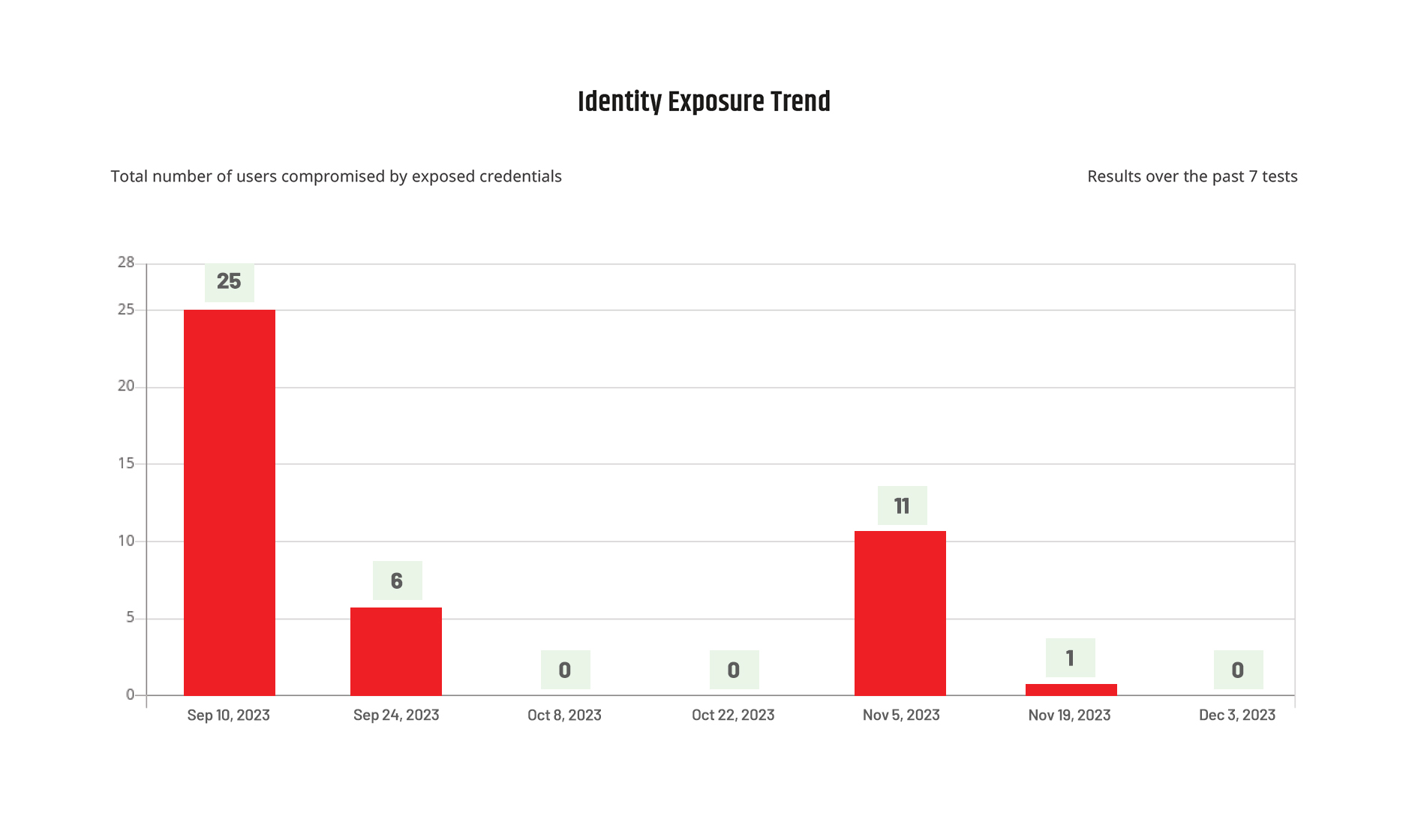
Get an accurate picture of which credentials attackers may be able to steal or crack to gain access to your systems, and which attacks they can perpetrate.
Validate leaked credentials against your entire attack surface
Continuously monitor real-world compromised credentials and test them safely against your complete attack surface, in your production environment, just as an attacker would.
Speed up the validation-remediation cycle
Define effective remediation actions based on proven exposures. Use our guided remediation process to quickly fix and minimize the impact of potential compromises.
Validate your entire attack
surface with the Pentera
Platform.
Fix the security gaps that really matter.

Your toolkit: Helpful resources for smarter security validation.
Find out for yourself.
Begin your security validation journey.



