Continuous Monitoring
Get the power to assess the ongoing security posture of your third parties—and respond to changing threats with objective, evidence-based data.
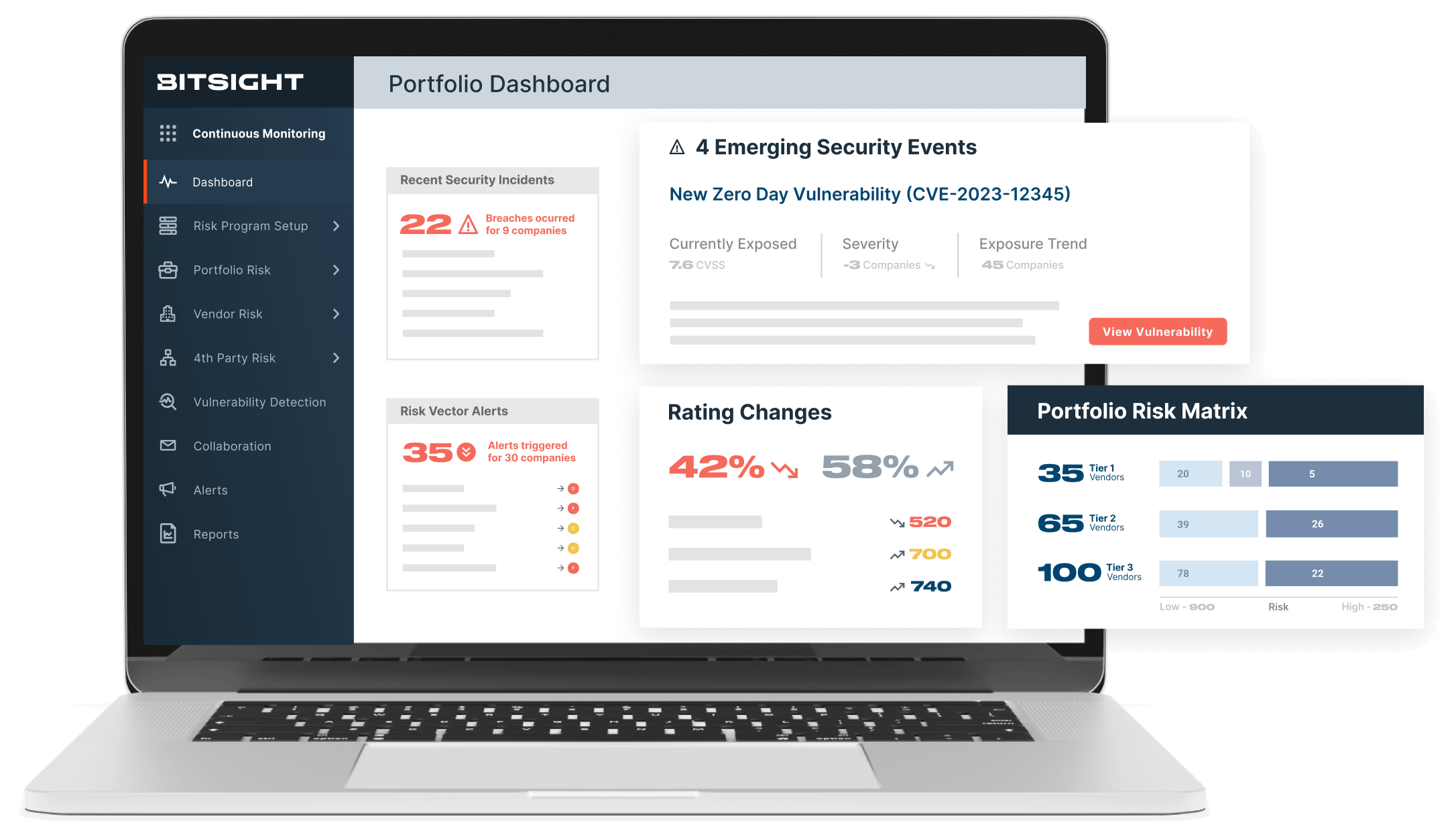
Stand strong: secure your business from third-party threats.
Supply chain attacks, zero days, and other cyber threats don’t wait for annual questionnaires or reassessments. To stay ahead, use Continuous Monitoring to keep a pulse on your vendor ecosystem and proactively mitigate risk. To understand and respond to third-party security gaps. And to take on more vendors to grow your business—while keeping complete visibility.
14
Bitsight analytics have statistically significant correlation with cybersecurity incidents.
10
Integrations with data feeds, VRM, and GRC tools for a flexible, end-to-end solution.
40M
Actively monitored organizations worldwide with cybersecurity data.
Time reduction assessing vendors*
Grow your business—without growing your staff.
Expanding your vendor ecosystem shouldn’t mean compromising on third-party risk management. Or needing excessive, expert resources. Bitsight arms you to identify, prioritize, and respond to vendor risk and exposure over time with unparalleled efficiency—whether it’s during routine monitoring or major security events.
Michael Christian
It used to take weeks to complete vendor assessments. Now it takes us hours. Bitsight Continuous Monitoring facilitates security discussions with potential vendors. It’s an integral part of our vendor risk management program.”
Identify, prioritize, and respond to vendor risk and exposure.
- Correlated Risk Vectors
- Extended Ecosystem Visibility
- Intigrated TPRM
- Effective Vendor Collaboration
- Vulnerability Detection & Response
Surface vendor risk insights
You need to focus on the highest risks. Bitsight risk vectors correlate to vendors’ likelihood of suffering from ransomware attacks or data breaches—so you can pin-point mitigation efforts.
- Leverage unparalleled data to make smarter decisions.
- Benefit from independent, proven correlation to cybersecurity incidents and stock performance.
Gain a holistic external view to your expanding footprint
View your attack surface the way the bad guys do. And see to the very edges of your risk surface—with automatic product discovery to manage fourth-party risk and detect areas of concentrated risk.
- Understand what products your vendors are most dependent on.
- Locate all your digital assets—including cloud services and shadow IT applications—and assess their risk.
- Minimize the impact of a fourth-party breach or exposure.
Increase efficiency across your workflows
No more switching between disparate tools and systems to manage your third-party risk program. Assess, onboard, and continuously monitor your third parties efficiently—in one place.
- Native integration with Bitsight VRM combines automated risk assessments with continuous monitoring.
- Accelerate your onboarding and assessment workflows in sync with your growing portfolio.
Partner with your third-parties for quicker remediation
Lead with high standards. Your vendors will follow. Use tangible, objective evidence on vendor exposure to guide collaborative efforts and increase confidence.
- Drive evidence-based collaboration for effective remediation.
- Centralize communication with vendors in one place.
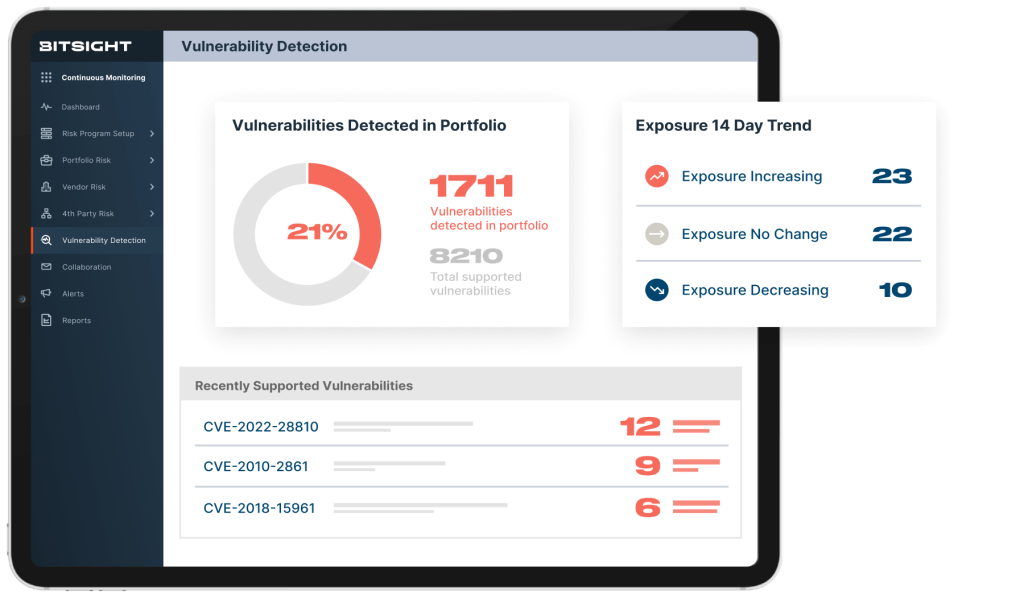
Mitigate third-party zero days at scale
When a major security event occurs, how do you assess and mitigate the impact across your portfolio? Tailored exposure evidence with scalable questionnaires—now that’s effective remediation.
- Initiate vendor outreach and track responses to critical vulnerabilities.
- Identify and prioritize exposed vendors with the most extensive third-party vulnerability research.
- Distribute templated questionnaires to your vendors to quickly assess exposure and increase response rate.

New Feature
Identify your vendors with a click of the button
With Vendor Discovery — the latest enhancement to Bitsight Continuous Monitoring — we surface relationships with both known and unknown vendors so you can identify hidden risk and take action more quickly.
Continuous Monitoring Resources




