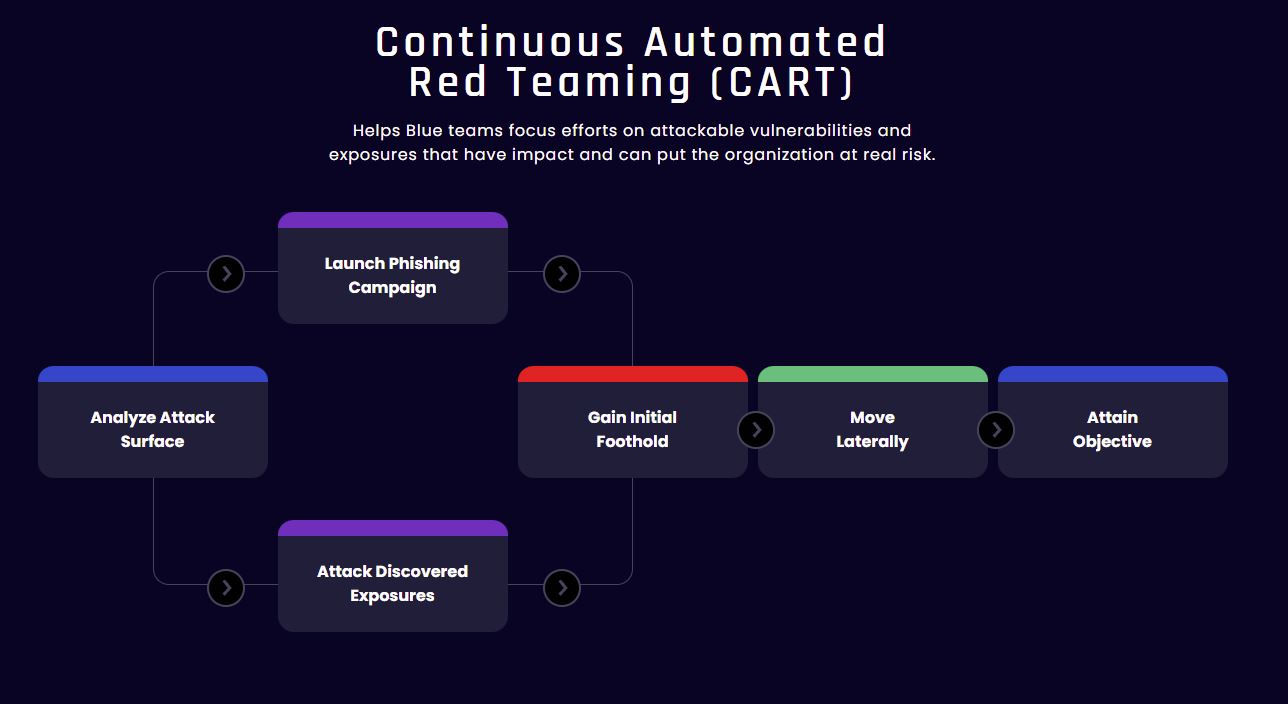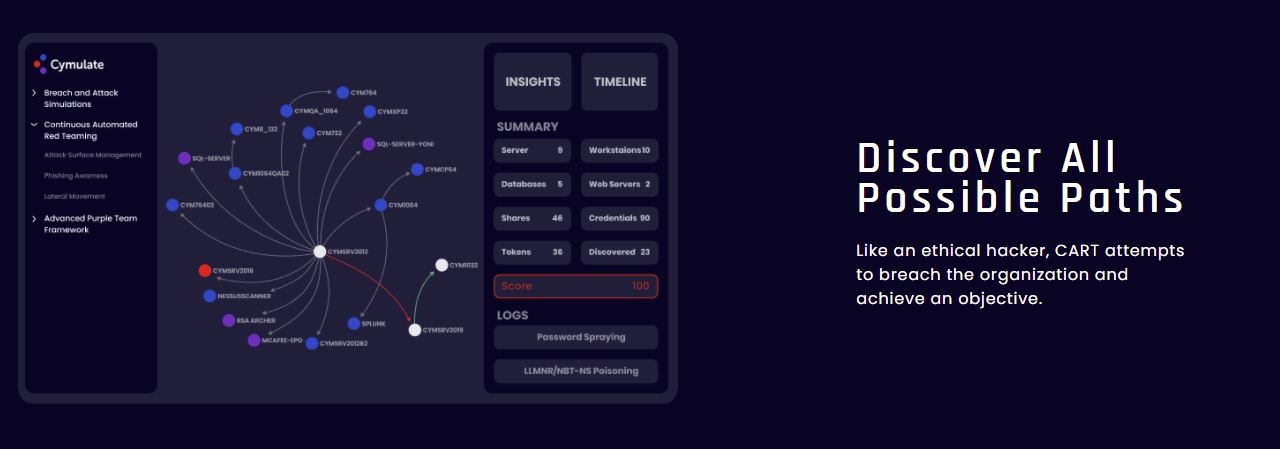
ATTACK SURFACE
Management (Recon)
Discover your digital footprint and know where you are exposed.
RISK BASED
Exposure Management
Know the impact of exploitable vulnerabilities, misconfigurations and phishing attacks on the organization.
CONTINUOUS
SOC Validation
Validate detection of automated red teaming attack campaigns. Improve and try again.