Delinea Account Lifecycle Manager
SERVICE ACCOUNT GOVERNANCE
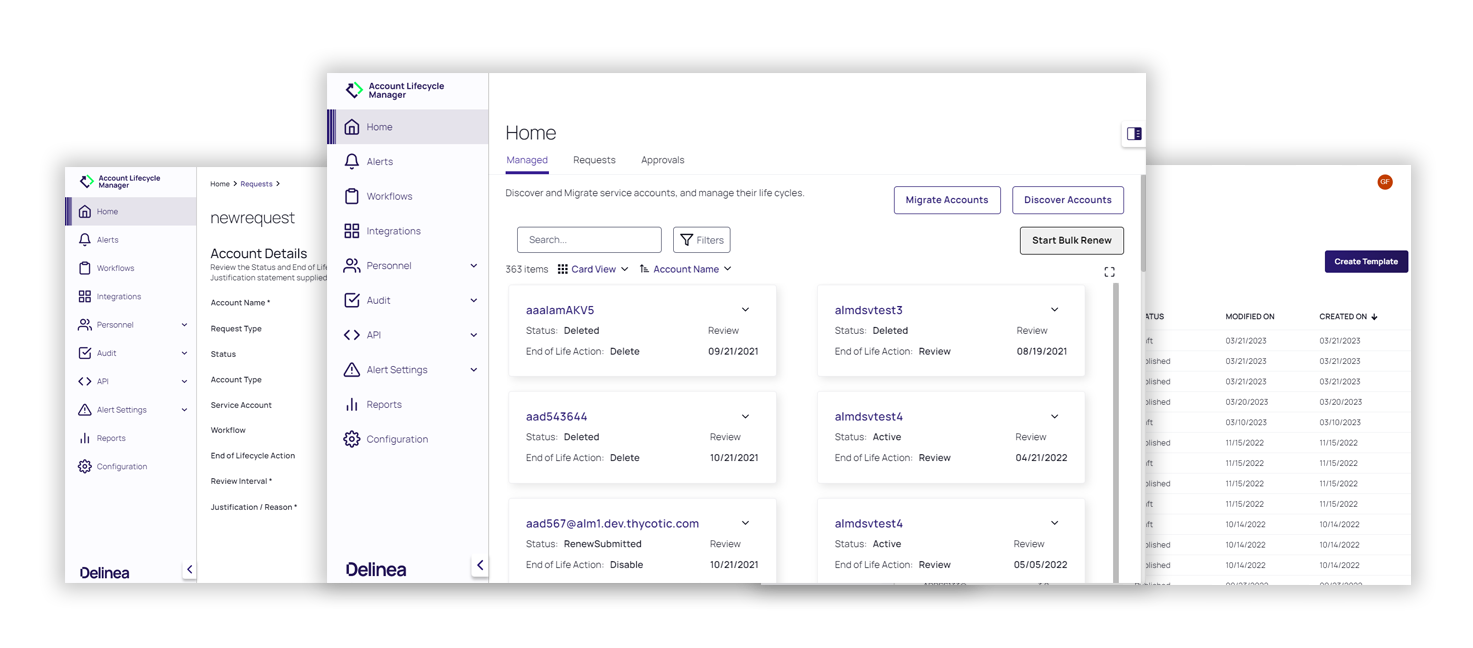
Account Lifecycle Manager
Seamless service account governance from discovery and provisioning through decommissioning.
Mitigate the risk of cyberattacks, service interruptions, and human error
Non-human privileged accounts access services, applications, data, and network resources.
Most service accounts fly under the radar of IT, expanding your vulnerable attack surface.
Automate service account governance to provide security teams with central oversight and control.
Increase accountability, consistency, and oversight of service account management
Control risky service account sprawl by automating and streamlining service account management.
Discover hidden accounts
Find and identify service accounts.
Establish workflows
Delegate ownership with role-based permissions.
Provision accounts
Set up accounts seamlessly and automatically.
Enforce governance
Establish ownership and accountability for accounts.
Decommission accounts
Remove accounts without causing disruption.
Account Lifecycle Manager
Try it for 30 days for Free Now
Sertalink needs the contact information you provide to us to contact you about our products and services. This way we can help you as best as possible.
BE: sales.be@sertalink.com
LUX: sales.lu@sertalink.com
Phone:
BE: +32(0)3.337.17.01
LUX: +352-27-94-06-59
Account Lifecycle Manager supports extended PAM
The standard definition of PAM isn’t sufficient for the growing risk of cyberattacks. We believe PAM must address the exploding number of identities and today’s IT complexities.
Our products provide effective authorization controls for an identity-centric approach to security.
