It’s more than a security rating. It’s a cyber risk story.
What is the Bitsight security rating?
The Bitsight Security Rating is a powerful tool used by security and risk leaders to assess, monitor, prioritize, and communicate cyber risk. It provides an objective, data-driven lens to view the health of an organization’s cyber security program.
Know that your attack surface is covered.
Fix immediate exposure issues while keeping an eye on what’s new in your company. And get to the root cause of EASM issues so you don’t see repeat problems. Now that’s long-term success.
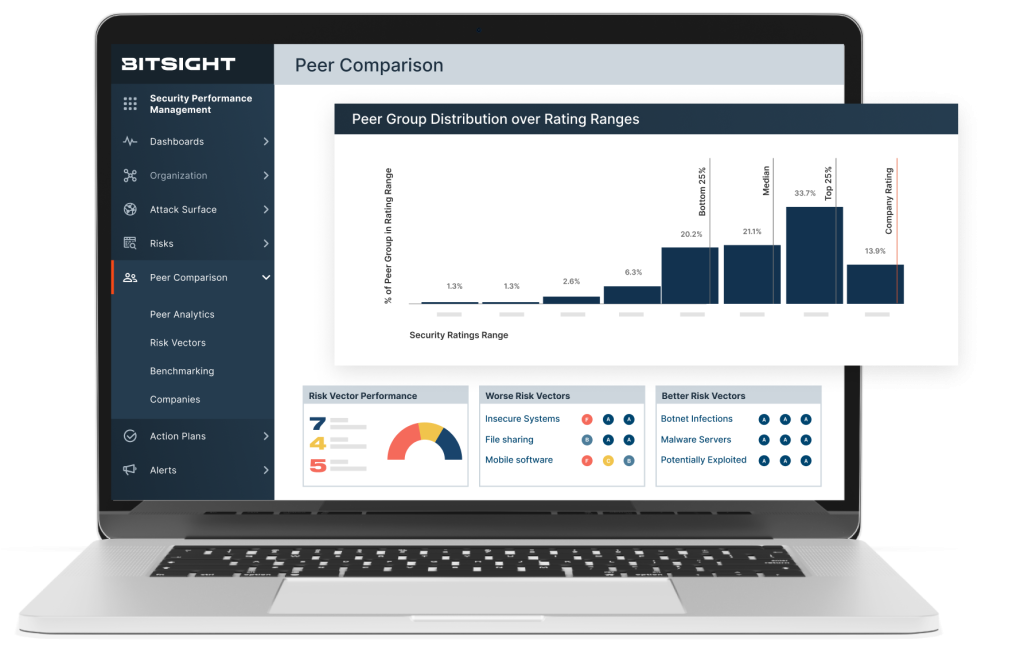
Categories of Risk
Bitsight categorizes cyber risk data into four primary categories as part of the collection and verification process.
Compromised
Systems
Indicates the presence of malware or unwanted software, which is evidence of security controls failing to prevent malicious or unwanted software from running within an organization.
Organizational
Diligence
Externally observable data about how servers and records in an organization are configured and provides insight into the security hygiene of an organization.
User
Behaviors
Employee activities that may introduce risks into an organization’s networks, such as sharing files over BitTorrent and determining if employees are re-using corporate login credentials outside of the corporate network.
Public
Disclosures
Information related to possible incidents of undesirable access to a company’s data, including breaches, general security incidents, and other disclosures.
Transparency
We build trust through transparency.Security Ratings Principles
Bitsight is committed to the “Principles for Fair and Accurate Security Ratings,” a series of practices developed alongside industry leaders to achieve transparency and trust in security ratings.
Bitsight Knowledge Base
The Bitsight Knowledge Base provides transparency on the methodologies, algorithms, calculations on other information regarding Bitsight’s cyber security rating
Dispute and Appeal
The Bitsight Policy Review Board (PRB) is a committee created to govern the ratings algorithm and associated policies, and to ensure that they are aligned with our principles.
Read more on The Bitsight Policy Review Board (PRB) →
It’s not only you. Your vendor risk matters.
The enterprise attack surface doesn’t end at the corporate firewall. As integration with more vendors accelerates, so too does the risk. The Bitsight Security Rating helps leaders see and take action on the third parties that introduce exposure for the enterprise.
See what others see.
How the Bitsight Security Rating is created.
We ingest over 400 billion events every day into Bitsight’s Cyber Risk Analytics Engine, leveraging a variety of tools and techniques including:
- Crawlers
- Sinkholes
- P2P network monitoring
- Honeypots
- BitTorrent monitoring
- Spam traps
- Darknet traffic monitoring
Our data collection methods continuously evolve to help you outpace the expanding threat landscape.
We then meticulously map our findings to entities to accurately build an organization’s network footprint. This includes:
- Company relationships
- Asset mapping
- IP and CIDR block mapping
- DNS mapping
- IP address mapping
- Subsidiary attribution
We monitor over 40 million organizations and maps 1 million entities.
Our threat research analysts apply a combination of artificial intelligence (AI) and human intelligence (HUMINT) to assess across risk vectors that have a known correlation to breach. We review things like:
- Botnet infections
- Spam infections
- Malware server
- PUPs , PUAS
- Pathing cadence
- TLS and SSL certificate config
- Open ports
- Software versioning
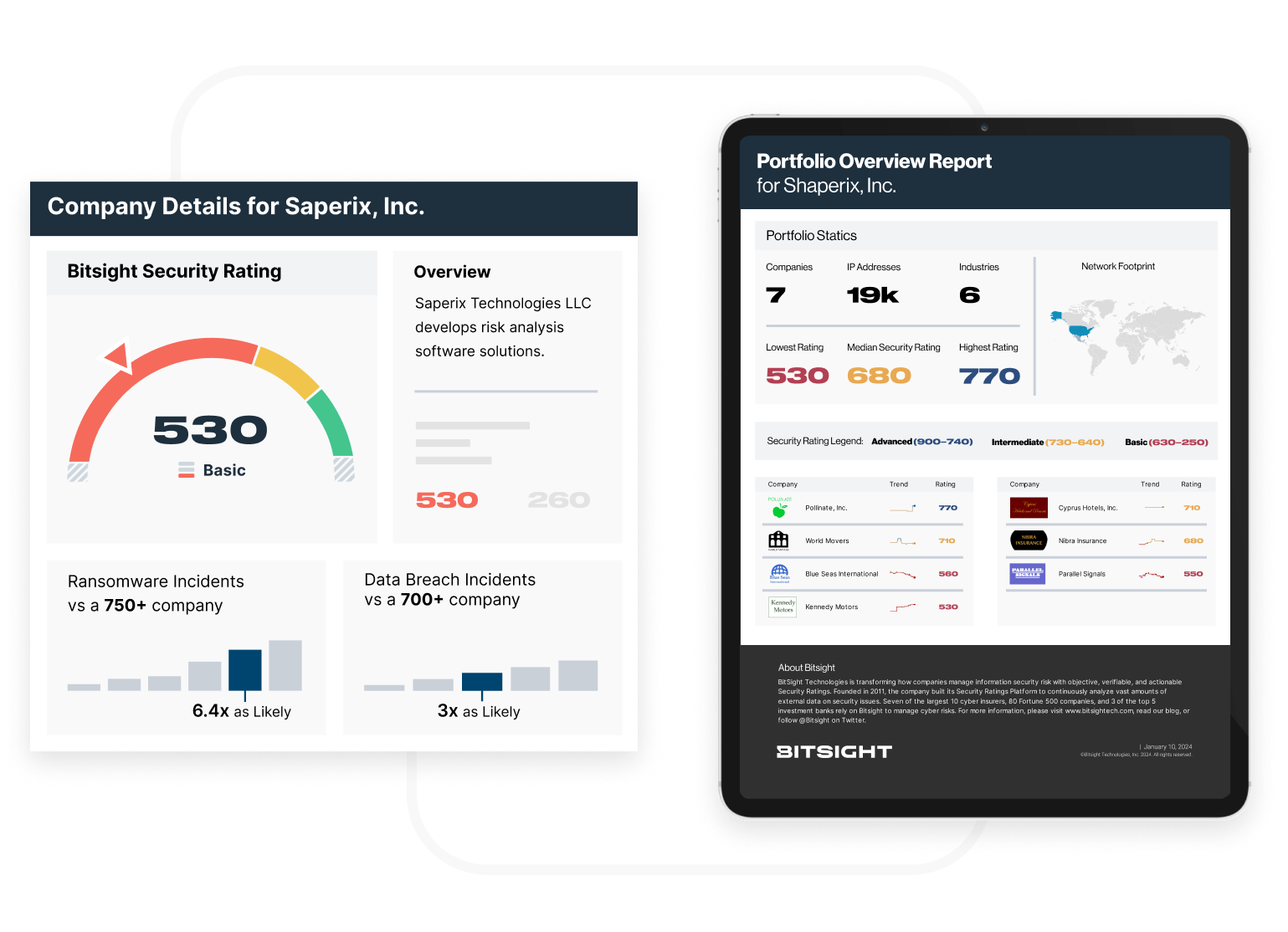
The final step is to communicate risk through a simple-to-consume rating on a scale from 300-820, analogous to a credit score. Letter grades are provided as well to provide an understanding of how a company is performing in each risk vector.
What makes the Bitsight Rating so special?
Bitsight data is independently verified to correlate with an organization’s risk of a security incident or data breach. See reports by AIR Worldwide, IHS Markiten Moody’s Analytics, demonstrating this critical connection.
