Phishing Simulation
Phishing Simulation Service
Train Your Employees to Recognize Phishing Attacks

Phishing Attacks Need to be Noticed
Email remains a primary threat vector. A recent report shows that 22% of breaches were caused by social actions or actions where the intent was to play on user or employee behavior. 96% of these social actions were delivered via email with 90% of those being classified as phishing. Even more concerning, 62% of what threat actors obtained through their successful phishing efforts were login credentials. Can your employees recognize a phishing email when they see one?

FortiPhish helps you address the risk posed by uninformed users. With the right testing and education, they can become a strong line of defense. When combined with learning reinforcement, your users will have the tools they need to recognize and respond appropriately to phishing and other social engineering efforts.
FortiPhish is a cloud-delivered phishing simulation service using deep knowledge of phishing techniques based on research by Fortinet FortiGuard Labs. This makes the phishing campaigns used to test users highly credible. FortiPhish also provides rich analytics to help administrators assess the susceptibility of users to phishing and related social engineering attacks. They can then identify users who may need extra support to get up to speed with your organization’s anti-phishing efforts.
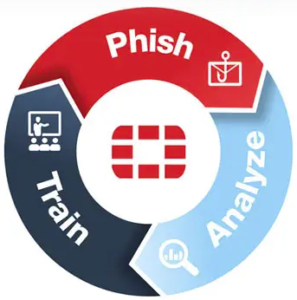
Key FortiPhish Use Cases

Phish your employees
Test awareness and vigilance across your users through real-world simulated phishing attacks while reinforcing proper practices at the point of click.
- Select the type of threat
- Select targeted users
- Schedule the simulated attack

Analyze campaign results
Analyze results and visualize program trends while identifying at-risk users and areas for improvement. Use results to adapt future training, further reinforcing vigilance across your organization.
- Analyze test results across users
- Address issues with users and report to leadership

Train your employees
Use findings to guide training for your users on the risks posed by email-borne threats and how to spot them. Threats include: phishing, spear phishing, whale phishing, pretexting, impersonation, and Business Email Compromise (BEC).
This component lets you leverage reporting to prioritize internal training programs and topics for your employees.
What’s In Your Email?
If your employees are clicking on malicious emails, your current email security solution is not stopping the malicious emails in the first place. Get a free Email Risk Assessment. It’s easy and we provide a detailed report outlining specific threats and risks across your employees.
