Complete
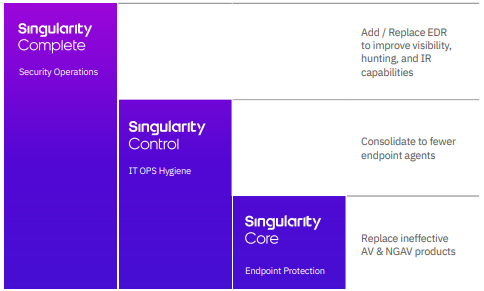
One Platform Solving More Problems
Organizations want more capability, less complexity, and fewer agents. SentinelOne delivers with rich EPP features within Singularity Complete.
In-Depth Visibility
Patented Storyline™ technology automatically tracks all OS relationships––benign and evil––every second of every day to provide analysts of all skill levels an easier way to understand root cause analysis and the complete attack story.
Lightens Analyst Load
Reduces manual investigation times and alert fatigue for SOC & IT analysts by automatically correlating telemetry and mapping it into the MITRE ATT&CK® framework.
Automated Threat Resolution
Efficient enterprise-grade ActiveEDR® simplifies response and automates resolution with patented, one-click remediation to reverse all unauthorized changes. No tedious scripting work.
One Agent for Consolidation Efforts
- Singularity Complete includes full featured enterprise-grade EDR.
- Complete includes NGAV and behavioral AI to stop known and unknown threats.
- Complete includes suite features like network control, USB device control, and Bluetooth device control.
- Complete includes Rogue identification and can be instrumented for full network attack surface protection with Ranger IoT.


Storyline Automates Visibility
- Storyline creates context in real time at the source: Windows, Mac, Linux, and Kubenetes cloud-native workloads.
- Storyline enables efficient hypothesis testing leading to fast RCA conclusions.
- Process re-linking across PID trees and across reboots preserves precious context.
- S1QL query language enables intuitive searches and hypothesis-based hunting.
ActiveEDR Automates Response
- ActiveEDR responses are part of the same code base as prevention mechanisms.
- Resolve threats with 1-Click and without scripting on one, several, or all devices across the entire estate.
- Mark benign findings as threats for the same real-time automatic, 1-Click remediation.
- Automated Storyline Active Response (STAR) watchlists keep a constant watch for noteworthy and customizable situations needing a deeper look.
- Single API with 350+ functions provides a basis for further automation.
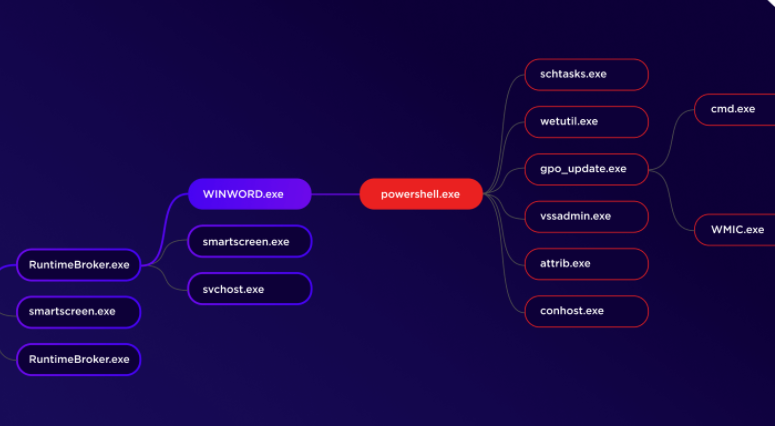
Hunter’s Toolkit
- High performance, industry leading historical EDR data retention. 14 to 365 days visibility.
- Deep Visibility Storyline pivot and hunt by MITRE ATT&CK® technique.
- Customizable network isolation
- Secure Remote Shell (full Windows Powershell. Standard Mac & Linux bash).
- Manual and auto file fetch of malicious and benign files for Windows, Mac, Linux. Optional sandbox integrations for additional dynamic analysis.
MDR Services Integration
- Vigilance MDR, our in-house global SOC, ensures every threat is reviewed, acted upon, documented, and escalated to you only when needed.
- Vigilance MDR PRO adds digital forensics investigative services (DFIR) for extended deep analysis and response.
- SentinelOne Readiness provides deployment assistance and quarterly ONEscore estate health grades and opportunities for improvement.