StealthAUDIT
The platform is the power behind the StealthAUDIT products. It has the automation, management, and integration building blocks that ensure the solutions’ advanced data collection and analysis deliver meaningful results to your team, your infrastructure, and your other technologies.
STEALTHbits has embraced this strategy and has evolved our products and features to help our customers implement a comprehensive DCAP security focus.
Once the types of data have been identified, and user access is understood, you can then start to make some decisions about restricting access to reduce risk and secure sensitive information.
Embracing a DCAP approach requires shifting the focus away from a siloed security stance to a more business informed focus data access. For more information on how STEALTHbits can provide the tools necessary to achieve a DCAP focus, visit the resource section at the bottom of this page.
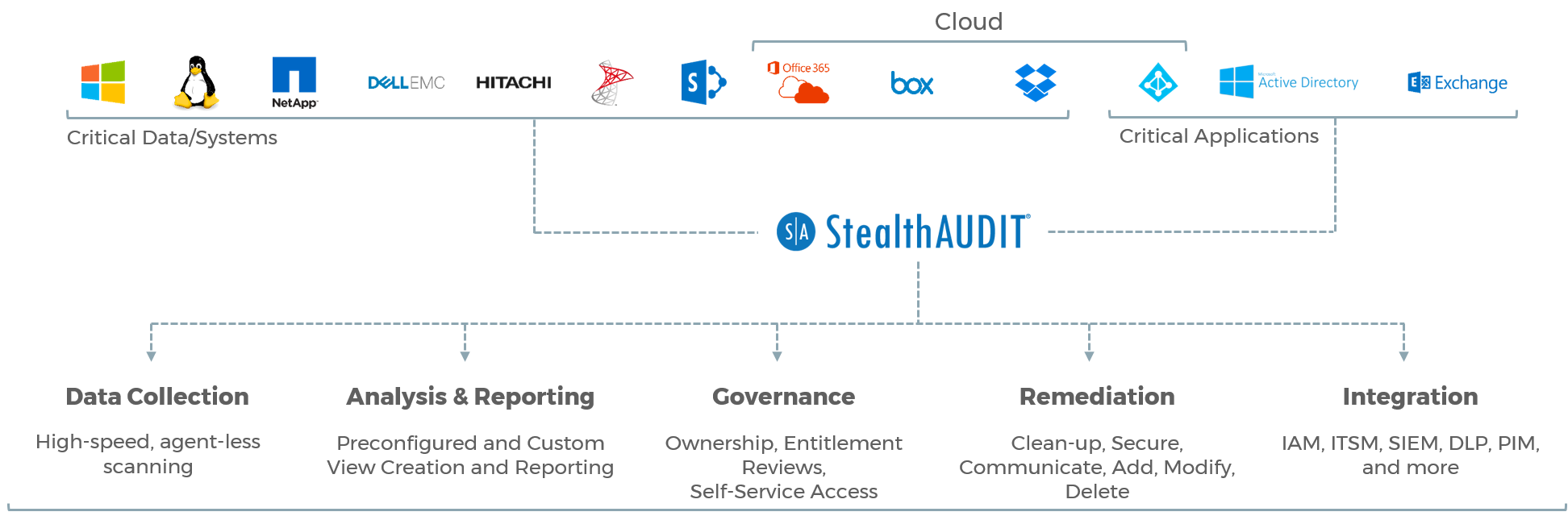
- Lightweight yet Scalable – Forged in the fires of the most demanding IT infrastructures in the world, StealthAUDIT is both lightweight enough to run everywhere it’s needed yet scalable enough to handle the load that spreading out far and wide brings.
- Seamless Integration – StealthAUDIT can push and pull data to and from dozens of technologies, including home-grown systems, to enhance the value of your other technology investments. Integrations with IAM, IAG, PIM, PAM, SIEM, CMDB, and other enterprise platforms are examples of how this integration is leveraged by our customers.
- Process Automation – StealthAUDIT seamlessly ties together disparate processes, creating fully automated solutions that save time, avoid unnecessary costs, and alleviate burden on IT.
- End-User Workflows – Not all the data you need comes from a system or application. When input and answers are required from actual human beings, StealthAUDIT provides simple, yet effective survey capabilities to retrieve and incorporate end-user feedback into the data analysis and decision-making process.
- Data Analysis – StealthAUDIT Analysis Modules allow you to slice-and-dice your data in every way possible, including correlation with existing and alternative data sources, easy-to-use view creation, historical trending, injection of business rules and logic, notification, exportation, and more. Users and consultants can also extend analysis with powerful SQL, PowerShell, and VB script inputs and exits.
- Powerful Reporting – Regardless of source, StealthAUDIT can report on any available dataset. Already have a reporting platform? StealthAUDIT can supply the comprehensive, fully integrated and analyzed data that your favorite reporting platform has been waiting for. Either way, your reports transform into the authoritative data you need to power insight and decisions.
